Chapter 3
Advanced Configuration
28
Wireless-N Gigabit Router
Firmware Upgrade
Before upgrading the firmware, download the Router’s
firmware upgrade file from the Linksys website,
www.linksys.com. Then extract the file.
Please select a file to upgrade the firmware
Click
Browse
and select the extracted firmware upgrade file.
Start to Upgrade
After you have selected the
appropriate file, click this button, and follow the on-screen
ff
instructions.
Status > Router
The
Router
screen displays information about the Router
r
and its current settings.
Status > Router
Router Information
Firmware Version
This is the version number of the
Router’s current firmware.
Current Time
This shows the time set on the Router.
Internet MAC Address
This is the Router’s MAC Address,
as seen by your ISP.
Host Name
If required by your ISP, this was entered on
the
Basic Setup
screen.
Domain Name
If required by your ISP, this was entered
on the
Basic Setup
screen.
Internet Connection
This section shows the current network information
stored in the Router. The information varies depending on
the Internet connection type selected on the
Basic Setup
screen.
Click
Refresh
to update the on-screen information.
Status > Local Network
The
Local Network
screen displays information about the
k
local, wired network.
Status > Local Network
Local Network
Local MAC Address
The MAC address of the Router’s
local, wired interface is displayed here.
Router IP Address
This shows the Router’s IP address, as
it appears on your local network.
Subnet Mask
This shows the Subnet Mask of the Router.
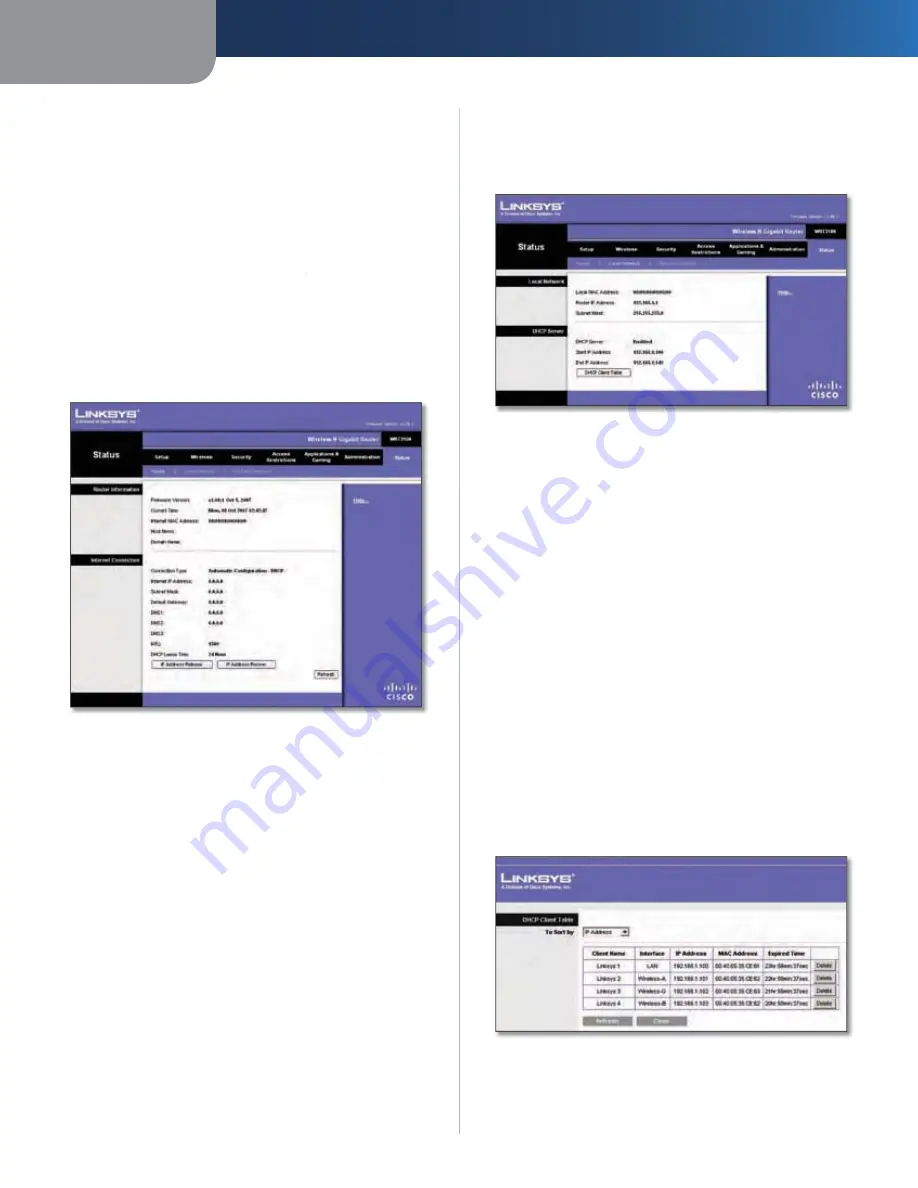
DHCP Server
DHCP Server
The status of the Router’s DHCP server
function is displayed here.
Start IP Address
For the range of IP addresses used by
devices on your local network, the starting IP address is
shown here.
End IP Address
For the range of IP addresses used by
devices on your local network, the ending IP address is
shown here.
DHCP Clients Table
Click this button to view a list of PCs
that are using the Router as a DHCP server.
DHCP Clients Table






























