Chapter 5
Setting Up and Configuring the Router
15
4-Port Gigabit Security Router with VPN
Firewall
From the Firewall Tab, you can configure the Router to
deny or allow specific internal users from accessing the
Internet. You can also configure the Router to deny or
allow specific Internet users from accessing the internal
servers. You can set up different packet filters for different
users that are located on internal (LAN) side or external
(WAN) side based on their IP addresses or their network
Port number.
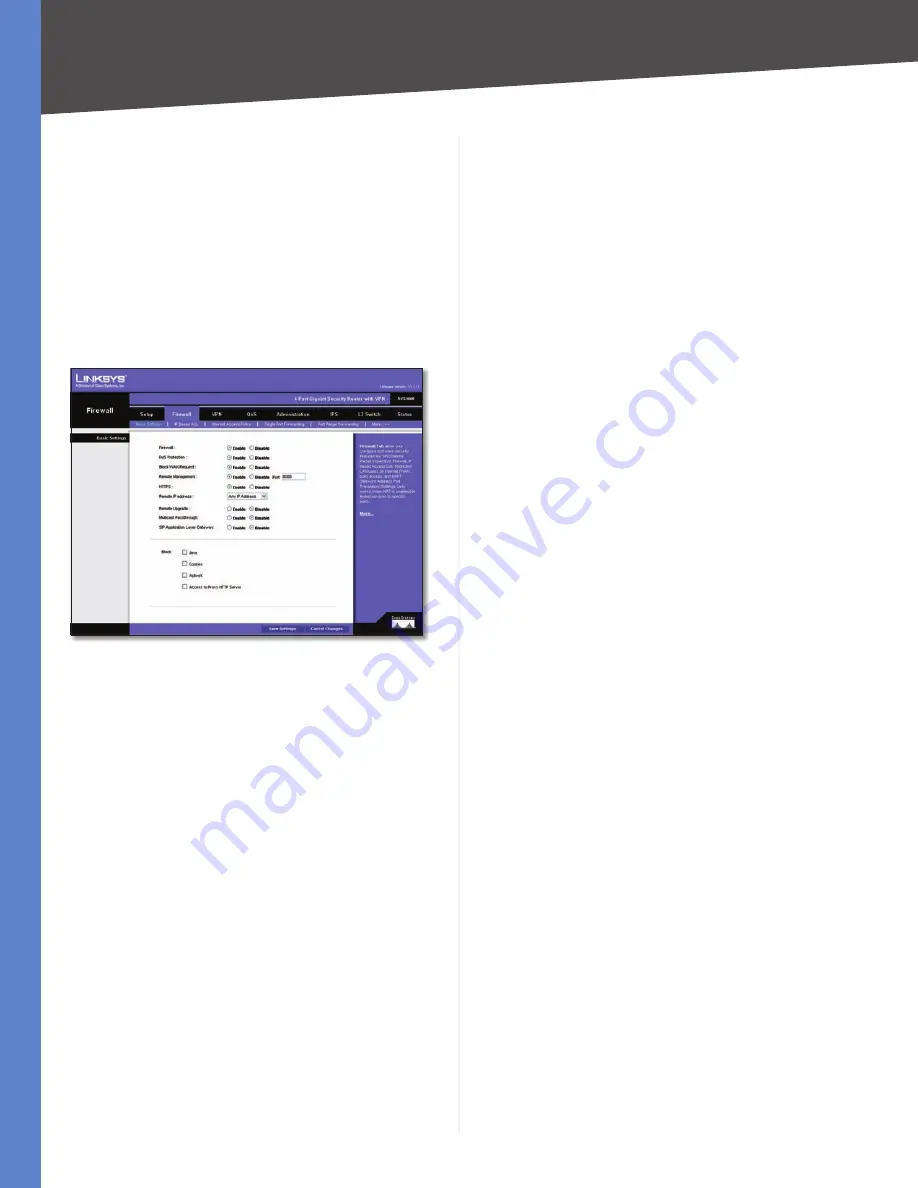
Firewall > Basic Settings
Firewall > Basic Settings
Firewall
When this feature is enabled, the Router’s NAT
firewall feature is enabled.
DoS Protection
When this feature is enabled, the Router
will block DoS (Denial of Service) attacks. A DoS attack
does not attempt to steal data or damage your PCs, but
overloads your Internet connection so you can not use it.
Block WAN Request
When this feature is enabled, the
Router filters out anonymous requests from the WAN.
Remote Management
This feature allows you to use
an http or https port to remotely manage the Router.
To enable this feature, select
Enable
and enter the port
number in the
Port
field, then configure the
HTTPS
and
Remote IP address
settings that appear below.
HTTPS
This option limits access to the Web-based Utility
from the WAN to https sessions only. An https session
uses SSL encryption, providing better protection for your
remote session than http. The default is
Enable
.
Remote IP address
•
Select the appropriate value to
specify which external IP address(es) can access the
Router:
Any IP Address
•
Allows access from any external IP
address.
Single IP Address
•
Allows access from the single IP
address that you enter in the field provided.
IP Range
•
Allows access from a range of IP addresses
that you enter in the field provided.
Subnet
•
Allows access from the Subnet that you enter
in the field provided.
Remote Upgrade
This option allows you to upgrade the
Router remotely. To allow remote upgrade, select Enable.
The Remote Management feature must be set to Enable
as well. The default is
Disable
.
Multicast Passthrough
If an IGMP Proxy running on the
Router, set this to Enable to cause the Router to allow IP
Multicast traffic to come in from the Internet. The default
is
Disable
.
SIP Application Layer Gateway
When this feature is
enabled, the SIP Application Layer Gateway (ALG) allows
Session Initiation Protocol (SIP) packets (used for Voice
over IP) to traverse the NAT firewall. This feature can be
disabled if the VoIP service provider is using other NAT
traversal solutions such as STUN, TURN, and ICE.
Block
Place a checkmark next to the Web features that
you wish to restrict.
Java
•
Java is a programming language for websites. If
you deny Java, you run the risk of not having access
to Internet sites created using this programming
language.
Cookies
•
A cookie is data stored on your PC and used
by Internet sites when you interact with them, so you
may not want to deny cookies.
ActiveX
•
ActiveX is a Microsoft (Internet Explorer)
programming language for websites. If you deny
ActiveX, you run the risk of not having access to
Internet sites using this programming language. Also,
Windows Update uses ActiveX, so if this is blocked,
Windows update will not work.
Access to Proxy HTTP Server
•
If local users have access
to WAN proxy servers, they may be able to circumvent
the Router’s content filters and access Internet sites
blocked by the Router. Denying Proxy will block access
to any WAN proxy servers.
Firewall > IP Based ACL
The IP-Based ACL screen allows you to create an Access
Control List (ACL) with up to 50 rules. Each ACL rule denies
or allows access to the network based on various criteria
including priority, service type, interface, source IP address,
destination IP address, day of the week, and time of day.






























