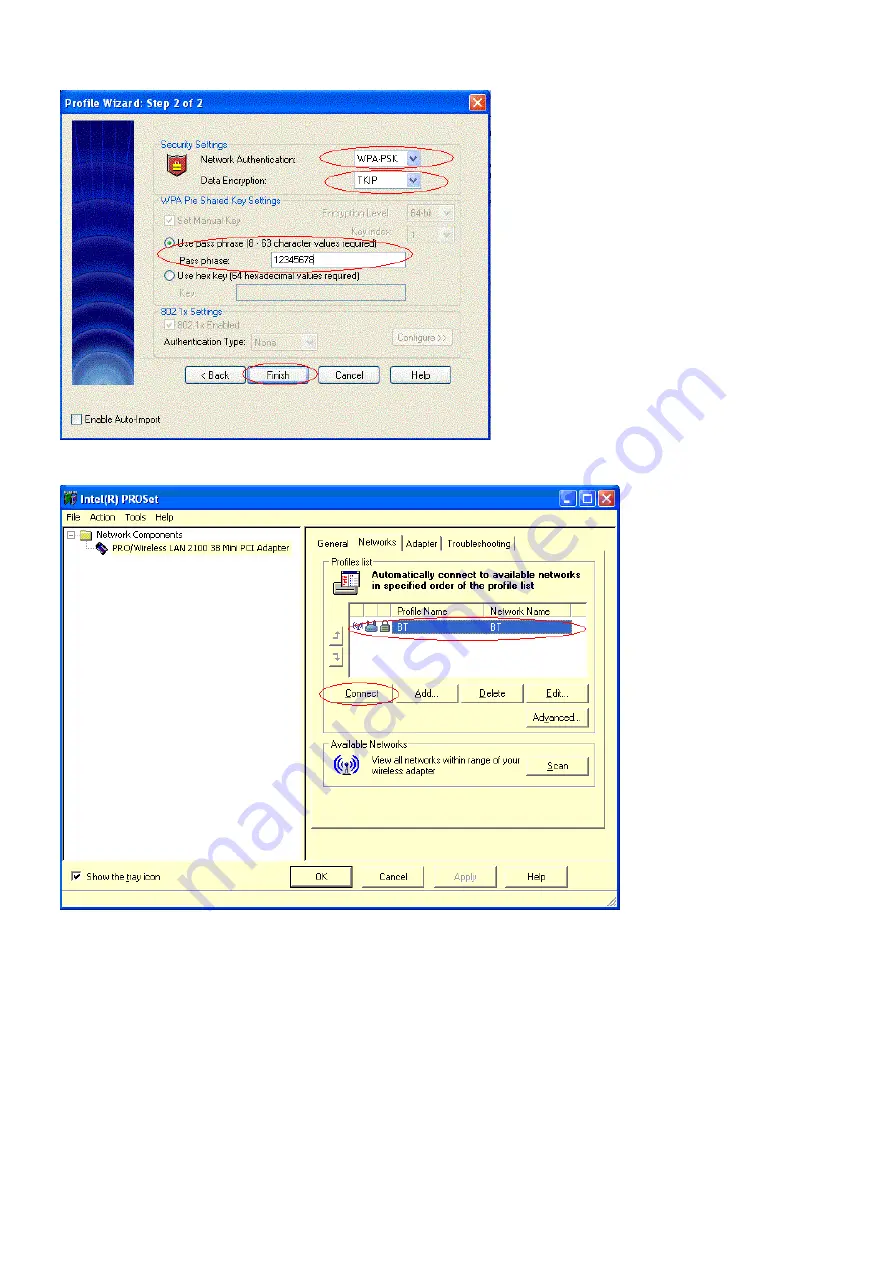
12. After you finished the profile settings, choose the profile you configured. Then, click Connect button to associate with the Access Point.
13. Click the General option, we will see the following information, that means the PC associated and authenticated with AP successfully.