Chapter 8 Licensing
UAG Series User’s Guide
134
You need to create an account at myZyXEL.com, register your UAG and then subscribe for
application patrol service in order to be able to download new packet inspection signatures from
myZyXEL.com (see the
Registration
screens). Use the
Signature Update > App Patrol
screen
to schedule or immediately download signatures.
• You need a valid service registration to update the App Patrol signatures.
• Schedule signature updates for a day and time when your network is least busy to minimize
disruption to your network.
• Your custom signature configurations are not over-written when you download new signatures.
Note: The UAG does not have to reboot when you upload new signatures.
Click
Configuration > Licensing > Signature Update > App Patrol
to display the following
screen.
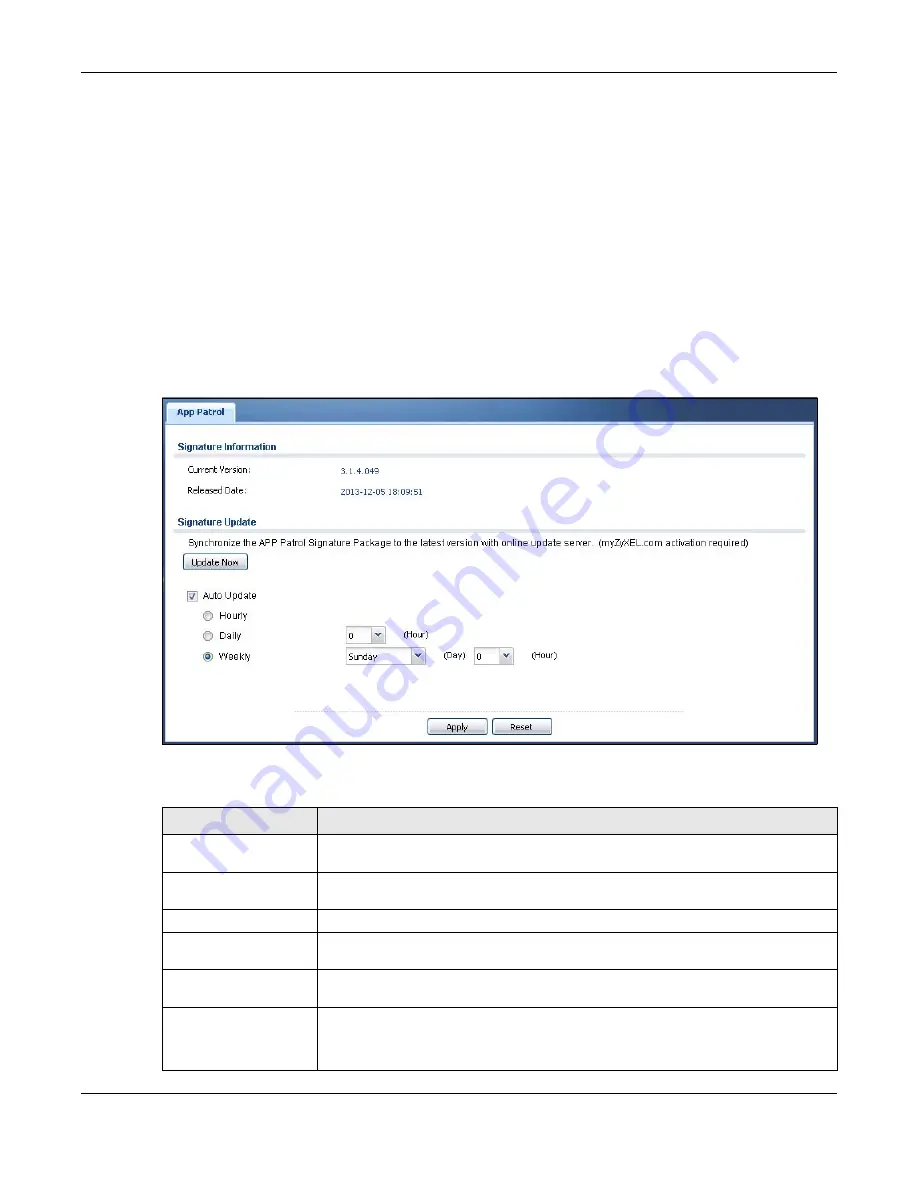
Figure 93
Configuration > Licensing > Signature Update > App Patrol
The following table describes the fields in this screen.
Table 52
Configuration > Licensing > Signature Update > App Patrol
LABEL
DESCRIPTION
Signature Information
The following fields display information on the current signature set that the UAG is
using.
Current Version
This field displays the signature and anomaly rule set version number. This number
gets larger as the set is enhanced.
Released Date
This field displays the date and time the set was released.
Signature Update
Use these fields to have the UAG check for new signatures at myZyXEL.com. If new
signatures are found, they are then downloaded to the UAG.
Update Now
Click this button to have the UAG check for new signatures immediately. If there are
new ones, the UAG will then download them.
Auto Update
Select this
check box
to have the UAG automatically check for new signatures
regularly at the time and day specified.
You should select a time when your network is not busy for minimal interruption.
















































