Always use the strictest Firewall settings for PPTP (also see
Section 2.6, “Firewalls and PPTP”
). Do
not
use the aXsGUARD
Gatekeeper
no-restrictions
and the
int-no-restrictions
Firewall
Policies as these seriously jeopardize your network security. These
policies should be used for testing or troubleshooting
only
and in a
network that is shielded from the Internet.
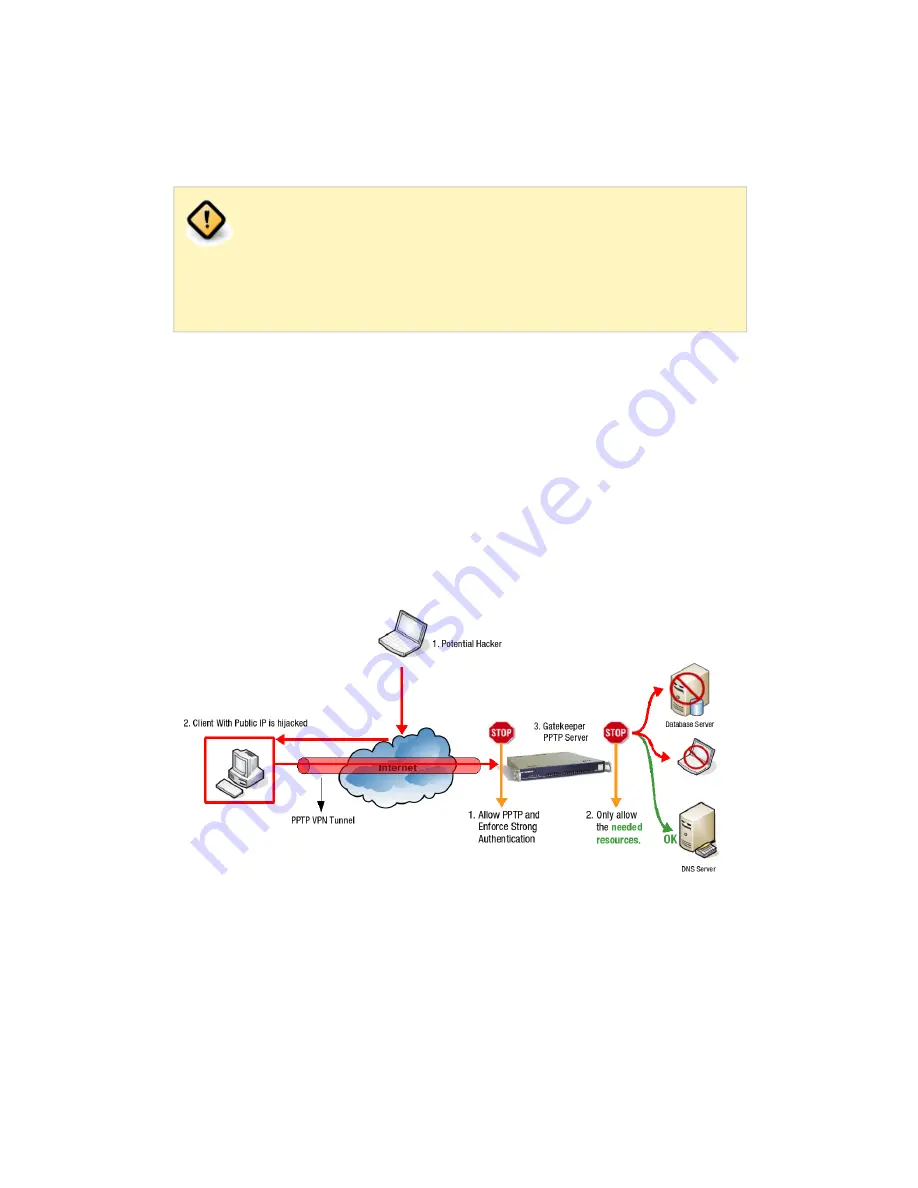
Firewall Rights determine which services, ports and hosts a user can or cannot
access. It is therefore critical to implement the strictest Firewall Policies on the
aXsGUARD Gatekeeper, to prevent damage in case the client’s computer is
compromized. Network traffic should be restricted to the resources that are
needed by the PPTP client, as illustrated below. The Firewall settings for the
aXsGUARD Gatekeeper PPTP service are configured in two stages:
• Allow PPTP traffic (and enforce Strong Authentication, e.g. DIGIPASS).
• Implement strict PPTP VPN Firewall Rules and restrict access to the
needed resources.
Both stages of the PPTP Firewall configuration are explained in
Section 3.6.2,
“Allowing PPTP Traffic”
and
Section 3.6.3, “Firewall Rights”
. An example is
provided in
Section 3.6.4, “Example of Firewall Settings for PPTP”
.
PPTP traffic must be allowed by the aXsGUARD Gatekeeper for clients to
successfully connect to the PPTP service. The
int-pptp-1
and
int-pptp-2
rules are
automatically added to the
stat-int
(system-wide) Firewall Policy when the PPTP
service is activated via System ⇒ Feature Activation ⇒ VPN & RAS. A validation
message as shown below is displayed. The Firewall rules
int-pptp-1
and
int-
pptp-2
open TCP port 1723 and allow GRE traffic (IP protocol ID 47). Both are
required for PPTP access.
3.6. PPTP Firewall Settings
3.6.1. Overview
Figure 3.5. Firewall Configuration
3.6.2. Allowing PPTP Traffic
© VASCO Data Security 2011
23






























