Shenzhen Ultrative Technology Co., Ltd.
T: +86-755-29685231
http://www.ultrative.cn | com
Add: 012#, 5/F, Block A, Hedong Bldg., Liutang Rd., Xixiang St., Bao An District, Shenzhen, China
89
/
97
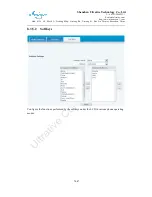
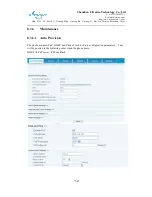
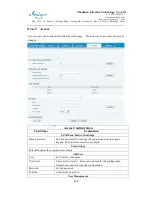
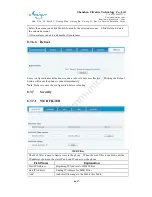
DMZ Configuration
Servers in a network most vulnerable to attack are those which provide services to users
outside the local network. Many times these computers are placed into their own
sub-network to provide more protection to the rest of the local network. This sub-network is
called a DMZ (taken from “demilitarized zone”). Computers in the DMZ have limited
connectivity to specific hosts in the internal network, although communication with other
hosts in the DMZ and to the external network is allowed. This allows hosts in the DMZ to
provide services to both the internal and external network, while a firewall controls the traffic
between the DMZ servers and the internal network clients.
The following chart describes the network access control of DMZ
.