SR808ac Cable Modem User Manual
55
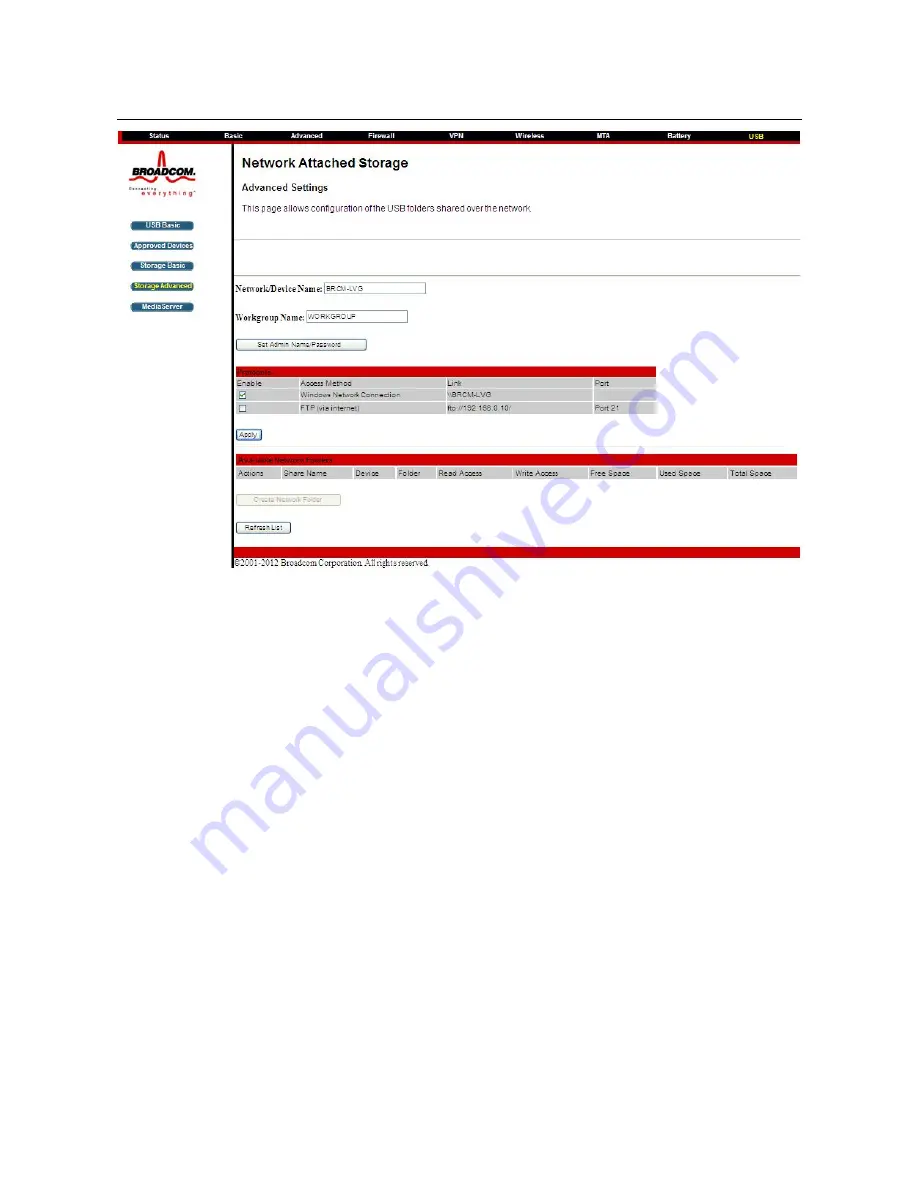
This page allows you to configure the device name. Additionally the workgroup name
can is configured here. The Windows Network and FTP support can be enabled or
disabled on this page. The IP address displayed in the link field is the Linux IP stack
address that should be used for the FTP server address in the FTP clients.
5.9.5
MediaServer
Choose
USB > MediaServer
to display the following page.



















