SR808ac Cable Modem User Manual
32
To enable the automatic email alerts, enter your email address in the space provided,
enter that email account’s associated SMTP (Outgoing) mail server address and
authentication credentials if required (provided by your ISP), check the “enable” box
and click the Apply button.
Individual emails will now be sent to the specified
address each time an attack is detected. Each attack is also logged in the table on
the Event Log page. If desired, a summary of the Event Log Table can be sent to the
specified contact email address by clicking on the Email Log button. Clicking on the
Clear Log button can also clear the table.
5.4.4
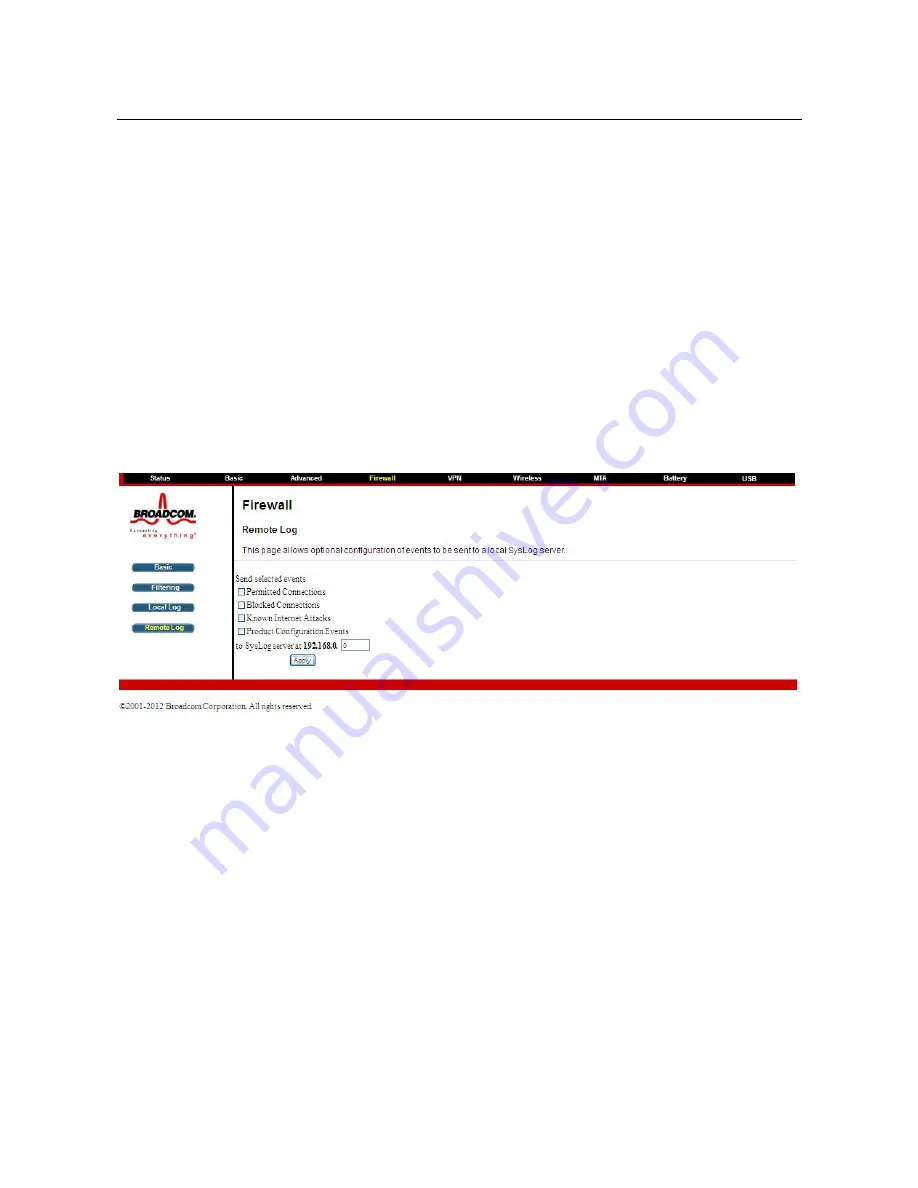
Remote Log
Choose
Firewall
>
Remote Log
to display the following page.
The Remote Log can send firewall attack reports out to a standard SysLog server so
many instances can be logged over a long period of time.
Individual attack or
configuration items can be selected that will be sent to the SysLog server such that
only the items of interest can be monitored.
Permitted connections, blocked
connections, known Internet attack types, and CMRG configuration events can be
logged.
The SysLog server must be on the same network as the Private LAN
behind the CMRG (typically 192.168.0.x). To activate the SysLog monitoring feature,
check all desired event types to monitor and enter the last byte of the IP address of
the SysLog server.
Normally, the IP address of this SysLog server would be
hard-coded so that the address will not change and always agrees with the entry on
this page.






























