129
5. Enhanced Network Security
Preventing Unauthorized Access
You can limit IP addresses, disable ports and protocols, or use Web Image Mon-
itor to specify the network security level to prevent unauthorized access over the
network and protect the address book, stored files, and default settings.
Enabling/Disabling Protocols
This can be specified by the network administrator.
Specify whether to enable or disable the function for each protocol.
By making this setting, you can specify which protocols are available and so pre-
vent unauthorized access over the network.
Preparation
For details about logging on and logging off with administrator authentica-
tion, see p.23 “Logging on Using Administrator Authentication”, p.26 “Log-
ging off Using Administrator Authentication”.
A
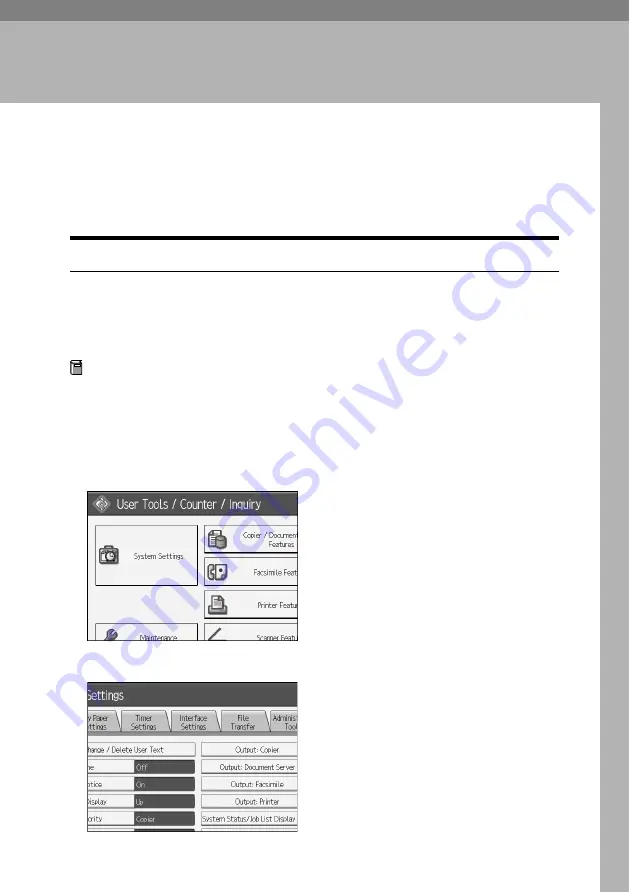
Press the
{
User Tools/Counter
}
key.
B
Press
[
System Settings
]
.
C
Press
[
Interface Settings
]
.






























