BM-525 Bandwidth Management Gateway User’s Manual
- 170 -
7.5 Log Backup
To save or receive the records that sent by the BM-525
STEP 1
﹒
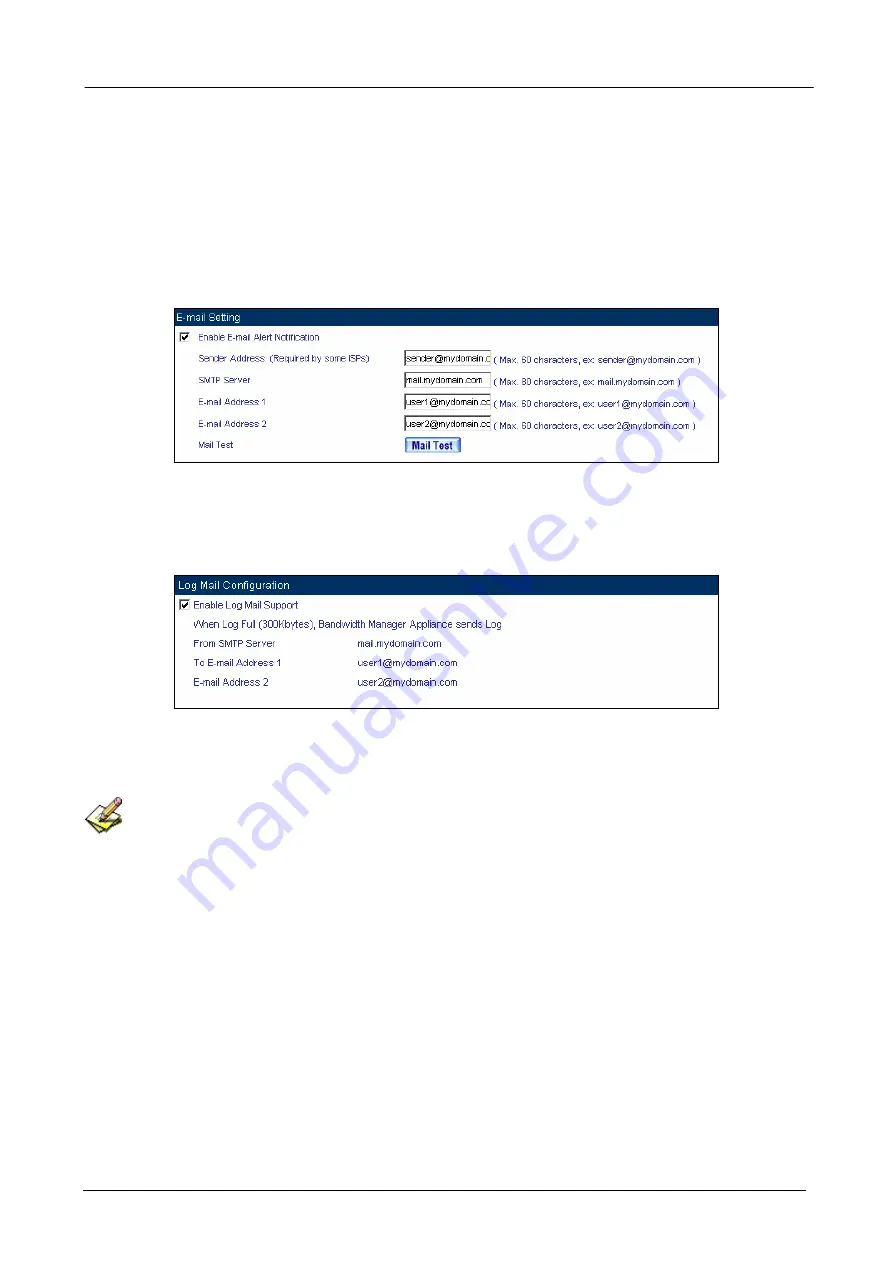
Enter
Setting
in
System
, select
Enable E-mail Alert Notification
function and set up
the settings.
E-mail Setting Web UI
STEP 2
﹒
Enter
Log Backup
in
Log
, select
Enable Log Mail Support
and click
OK
Log Mail Configuration Web UI
After
Enable Log Mail Support,
every time when
LOG
is up to 300Kbytes and it will accumulate
the log records instantly. And the device will e-mail to the Administrator and clear logs automatically.
Summary of Contents for BM-525
Page 181: ...BM 525 Bandwidth Management Gateway User s Manual 176 Outbound Source IP Statistics Report ...
Page 187: ...BM 525 Bandwidth Management Gateway User s Manual 182 Inbound Top Users Statistics Report ...
Page 202: ...BM 525 Bandwidth Management Gateway User s Manual 197 Interface Status ...






























