UidPwdDirAuth Plug-in Module
Chapter
1
Authentication Plug-in Modules
23
directory in an HTML form that is served by a Certificate Manager or Registration
Manager (see “Enrollment Forms” on page 53). Once the server successfully
authenticates an end user, it retrieves the rest of the information required to
formulate the certificate from the directory.
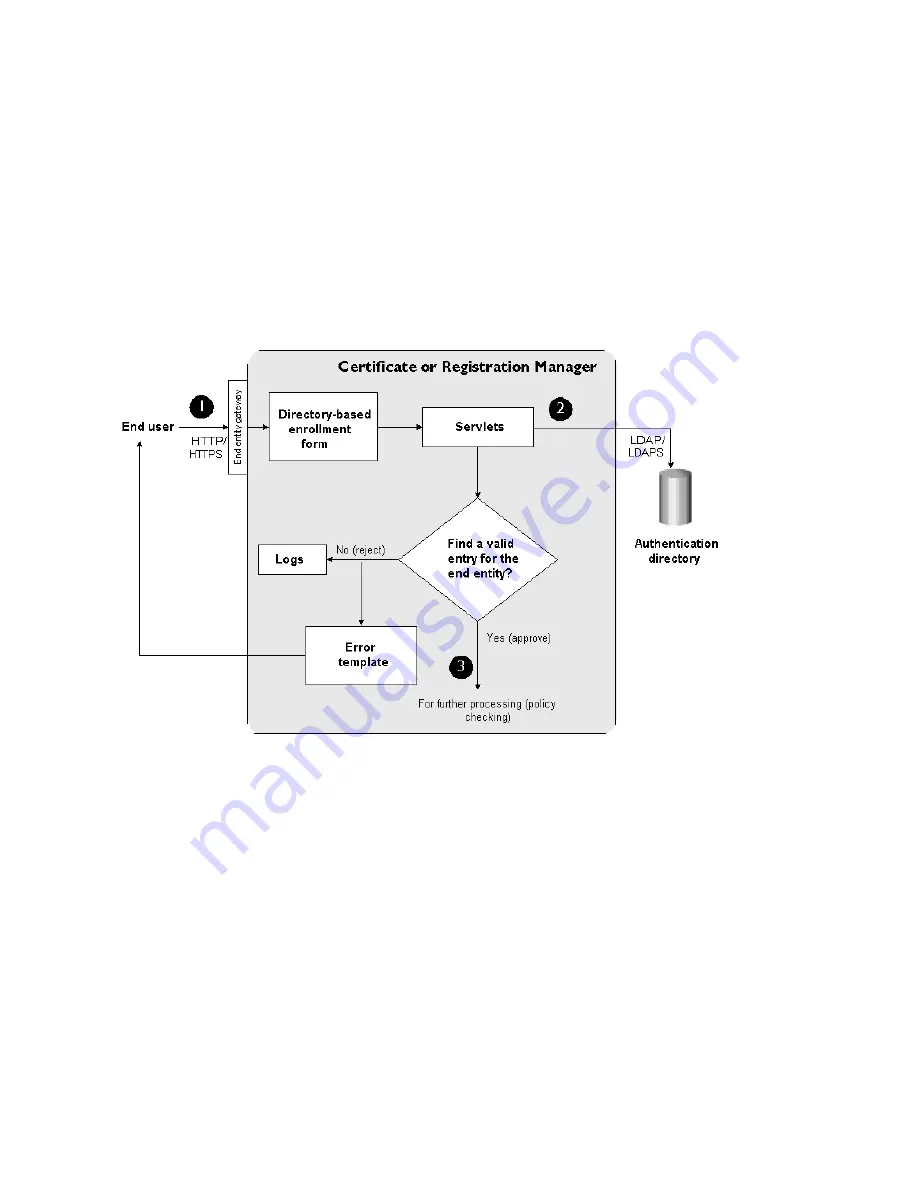
Figure 1-3 illustrates how authentication based on a user ID and password works
during certificate enrollment.
Figure 1-3
User ID- and password-based authentication of an end user
These are the steps shown in Figure 1-3:
1.
In the directory-based certificate enrollment form, the end user enters a user ID
and password for the directory and submits the request to a Certificate
Manager or Registration Manager.
2.
When the server receives the request, it looks up the directory that is
configured for authenticating end users. The server verifies the authenticity of
the user by checking the directory entries.
❍
If the end user does not have a valid entry in the directory, the server
rejects the request, logs an error message, and sends a rejection notification
to the user.
Summary of Contents for Certificate Management System 6.0
Page 1: ...Plug Ins Guide Netscape Certificate Management System Version6 0 March 2002...
Page 10: ...10 Netscape Certificate Management System Plug Ins Guide March 2002...
Page 62: ...Enrollment Forms 62 Netscape Certificate Management System Plug Ins Guide March 2002...
Page 308: ...NTEventLog Plug in Module 308 Netscape Certificate Management System Plug Ins Guide March 2002...






























