Chapter 3
Advanced Configuration
3
Wireless-N Ethernet Bridge with Dual-Band
Chapter 3:
Advanced Configuration
After setting up the Bridge with the Setup Wizard (located
on the CD-ROM), the Bridge will be ready for use. However,
if you want to change its advanced settings, use the
Bridge’s web-based utility. This chapter describes each
web page of the utility and each page’s key functions. You
can access the utility via a web browser on a computer
networked with the Bridge.
The web-based utility has these main tabs: Wireless,
Network Setup, Administration, and Status. Additional
tabs will be available after you click one of the main tabs.
How to Access the Web-Based Utility
Use a web browser to access the web-based utility.
If the Bridge is connected to a network with a DHCP server
(usually the network router), then the Bridge will obtain
its IP address from the DHCP server. If there is no DHCP
server, then the Bridge will use its default static IP address,
169.254.1.250
. (If you set a permanent static IP address
on the Bridge through the web-based utility, then enter
the static IP address instead.)
NOTE:
If you do not know the Bridge’s IP address,
then find its IP address in the DHCP clients table
of your router. (Refer to the documentation for
your router.)
If you cannot locate the Bridge’s IP address, you
can reset the Bridge; press the
Reset
button
on the Bridge for approximately five seconds,
using a straightened paper clip. This will reset
the Bridge back to the factory default settings.
The Bridge will request an IP address from the
DHCP server (usually the network router). If no
DHCP server is found, then the Bridge will use
its default static IP address,
169.254.1.250
,
until it detects a DHCP server and is assigned a
dynamic IP address.
If the Bridge is not associated with a router and is using
the factory default settings, connect a computer to
the Bridge using an Ethernet connection to access the
web-based utility. You will need to configure the Ethernet
connection on the computer with a static IP address and
subnet mask.
The IP address of your Ethernet adapter should be set to a
specific IP address.
In the
1.
IP address
field, enter
169.254.x.y
(x should
be replaced by a number between 1 and 254, and y
should be replaced by a number between 0 and 255).
In the
2.
Subnet mask
field, enter
255.255.0.0
.
NOTE:
The steps to assign a static IP address to
the Ethernet adapter on your computer vary by
operating system. For instructions, please refer
to the help documentation of your specific
operating system.
After you have assigned your Ethernet adapter with a
static IP address, launch your web browser, and enter the
Adapter’s IP address (the default setting is
169.254.1.250
)
in the
Address
field. Press
Enter
.
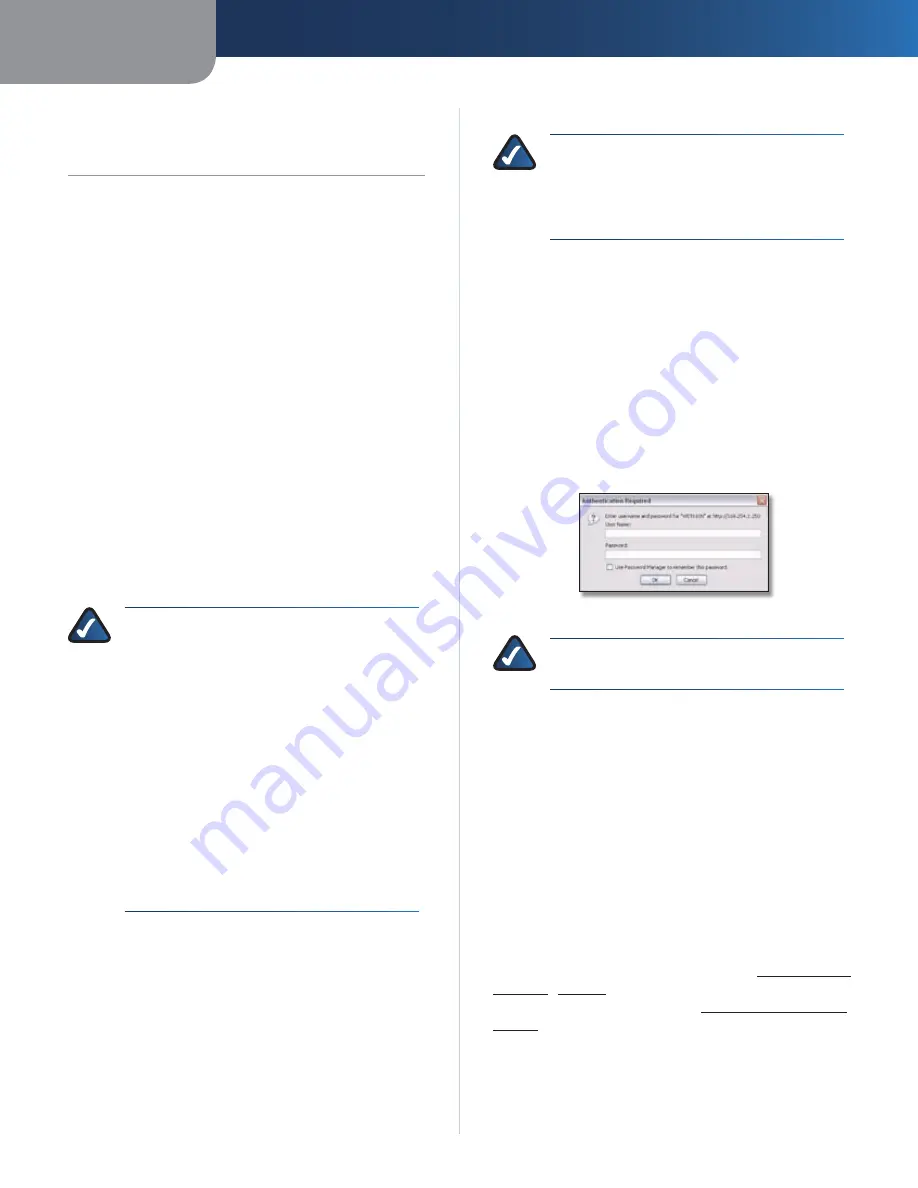
A password request screen appears. (Non-Windows XP
users will see a similar screen.) Leave the
User name
field
blank. Enter the password you created during the Setup
Wizard. If you did not create a new password, use the
default password
admin
. (You can set a new password
from the
Administration >
Management
screen.) Click
OK
to continue.
Password Screen
NOTE:
If the password request screen does not
appear, wait two minutes and try again.
Wireless > Basic Wireless Settings
The first screen that appears is the
Basic Wireless Settings
screen. Configure the basic wireless and security settings
on this screen.
There are two ways to configure the Bridge’s settings,
manual and Wi-Fi Protected Setup. Wi-Fi Protected Setup
is a feature that makes it easy to set up your wireless
network. If your network router supports Wi-Fi Protected
Setup and uses WPA or WPA2 security, then you can
use Wi-Fi Protected Setup to automatically connect the
Bridge.
Wireless Configuration
To manually configure your
wireless network, select
Manual
. Refer to
Basic Wireless
Settings
,
page 4
. To use Wi-Fi Protected Setup, select
Wi-Fi Protected Setup
. Refer to
Wi-Fi Protected Setup
,
page 5
.







































