iSG4F
User’s Manual
iS5 Communications Inc.
49
12.2
Local Clock Commands Description
Command
Description
Config terminal
date
{[YYYY.]MM.DD-hh:mm[:ss] |
hh:mm[:ss]}
Sets the current time and date.
date
Show the system time
12.3
Set Local Clock Example
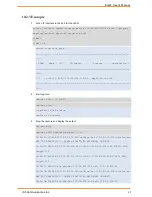
1.
Example for time configuration
iSG4F#date 2014.02.02-10:01:30
Sun Feb 2 10:01:30 UTC 2014
Current RTC date/time is 2-2-2014, 10:01:30.
iSG4F# date
Sun Feb 2 10:01:34 UTC 2014
ACLs
ACLs (Access Control Lists) filter network traffic by controlling whether routed packets are
forwarded or blocked at the router's interfaces. ACLs are used to block IP packets from being
forwarded by a router. The router examines each packet to determine whether to forward or
drop the packet, based on the criteria specified within the access lists. Access list criteria can
be the source address of the traffic, the destination address of the traffic, the upper-layer
protocol or other information.
There are many reasons to configure access lists - access lists can be used to restrict contents
of routing updates or to provide traffic flow control. But one of the most important reasons to
configure access lists is to provide security for the network. Access lists must be used to
provide a basic level of security for accessing the network. If access lists has not been
configured on the router, all packets passing through the router can be allowed onto all parts
of the network. For example, access lists can allow one host to access a part of the network
and prevent another host from accessing the same area.