Chapter 6. Compliance subsystem implementation
173
The way this collector works depends on the data you have provided as
parameters.
It first checks for the key existence if one is specified. Then it checks if the
value is specified. Finally, if both are found, it verifies the rules specified in
VALUE_DATA_RULES. There may be one or more rules specified. The
construction of the rules is described below.
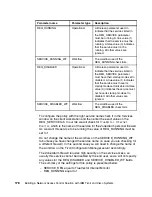
VALUE_DATA_RULES
Operational
If the registry key specified in the KEY parameter and the
registry value specified in the VALUE parameter both
exist, then the contents of this parameter are used to
determine the status of the registry value data check. The
VALUE_DATA_RULES parameter should contain zero or
more parameter values that make up the rules. Rules will
be explained in more detail in a later section.
DEFAULT_RULE
Operational
Used by the collector to determine the status of various
checks if a specific rule does not apply. No more than one
parameter value should be provided. If more than one
parameter value is provided, only the first parameter
value will be used. The parameter value provided should
be one of the following: PASS, WARN, or FAIL. If the
parameter value is set to either WARN or FAIL, then a
workflow may be used. If the parameter value is set to
something other than PASS, WARN, or FAIL, errors may
occur. If no parameter value is provided, this parameter
defaults to PASS.
KEY_WF
Workflow
Contains the data attached to any workflow that is
generated by the registry key existence check. Zero or
more parameter values may be provided.
VALUE_WF
Workflow
Contains the data attached to any workflow that is
generated by the registry value existence check. Zero or
more parameter values may be provided.
VALUE_DATA_WF
Workflow
Contains the data attached to any workflow that is
generated by the registry value data check. Zero or more
parameter values may be provided.
Parameter name
Parameter type
Description
Summary of Contents for Tivoli and Cisco
Page 2: ......
Page 16: ...xiv Building a Network Access Control Solution with IBM Tivoli and Cisco Systems...
Page 18: ...xvi Building a Network Access Control Solution with IBM Tivoli and Cisco Systems...
Page 20: ...2 Building a Network Access Control Solution with IBM Tivoli and Cisco Systems...
Page 30: ...12 Building a Network Access Control Solution with IBM Tivoli and Cisco Systems...
Page 56: ...38 Building a Network Access Control Solution with IBM Tivoli and Cisco Systems...
Page 94: ...76 Building a Network Access Control Solution with IBM Tivoli and Cisco Systems...
Page 110: ...92 Building a Network Access Control Solution with IBM Tivoli and Cisco Systems...
Page 142: ...124 Building a Network Access Control Solution with IBM Tivoli and Cisco Systems...
Page 225: ...Chapter 6 Compliance subsystem implementation 207 Figure 6 77 Client connection window...
Page 456: ...438 Building a Network Access Control Solution with IBM Tivoli and Cisco Systems...
Page 458: ...440 Building a Network Access Control Solution with IBM Tivoli and Cisco Systems...
Page 504: ...486 Building a Network Access Control Solution with IBM Tivoli and Cisco Systems...
Page 513: ...Building a Network Access Control Solution with IBM Tivoli and Cisco Systems...
Page 514: ......
Page 515: ......