64
Expert Power Control 8316
© 2022 GUDE Systems GmbH
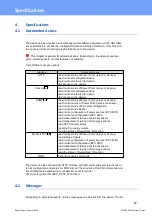
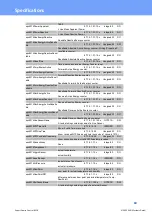
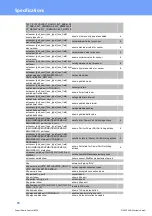
Specifications
The interaction of TLS 1.3 and unsecure certificates and a web browser with Chromium
Engine (Google Chrome or MS Edge) can lead to performance losses, and thus longer
loading times. In this constellation, the Chromium Engine does not correctly support the
SSL Session Cache (Session Tickets) and the math unit of the embedded CPU may be
overwhelmed with continuous RSA operations. There are some possible workarounds:
·
Use secure certificates (official certificate authority or marked as secure in the OS)
·
or use of the Firefox browser
·
or use of ECC 256 (no RSA) certificates
·
or configure to "TLS v1.2 only
Creating your own Certificates
The SSL stack is supplied with a specially newly generated self-signed certificate. There is no
function to generate the local certificate anew at the touch of a button, since the required ran-
dom numbers in an embedded device are usually not independent enough. However, you can
create new certificates and import them to the device. The server accepts RSA (2048/4096)
and ECC (Elliptic Curve Cryptography) certificates.
Usually OpenSSL is used to create an SSL certificate. For Windows for example, there is the
light version of
. There you open a command prompt, change to
the directory "C:\OpenSSL-Win32\bin" and set these environment variables:
set openssl_conf=C:\OpenSSL-Win32\bin\openssl.cfg
set RANDFILE=C:\OpenSSL-Win32\bin\.rnd
Here are some examples for the generation with OpenSSL:
Creation of a self-signed RSA 2048-bit certificate
openssl genrsa -out server.key 2048
openssl req -new -x509 -days 365 -key server.key -out server.crt
RSA 2048-bit certificate with Sign Request:
openssl genrsa -out server.key 2048
openssl req -new -key server.key -out server.csr
openssl req -x509 -days 365 -key server.key -in server.csr -out server.crt
The server keys should be created with "openssl genrsa". The Gude device pro-
cesses keys in the traditional PKCS#1 format. This can be recognized by the fact that
the generated key file starts with "-----BEGIN RSA PRIVATE KEY-----". If the file starts
with "-----BEGIN PRIVATE KEY-----", the file is in PKCS#8 format and the key is not re-
cognized. If you have only a key in PKCS#8 format, you can convert it to PKCS#1 with
openssl: "
openssl rsa -in pkcs8.key -out pkcs1.key
".
ECC Certificate with Sign Request:
openssl ecparam -genkey -name prime256v1 -out server.key
openssl req -new -key server.key -out server.csr
openssl req -x509 -days 365 -key server.key -in server.csr -out server.crt
Summary of Contents for Expert Power Control 8314
Page 2: ...2 Expert Power Control 8316 2022 GUDESystems GmbH ...
Page 5: ...Device Description ...
Page 12: ...Operating ...
Page 23: ...Configuration ...
Page 51: ...Specifications ...
Page 104: ...104 Expert Power Control 8316 2022 GUDESystems GmbH Specifications ...
Page 105: ...Support ...