P a g e
|
28
UCM Security Manual
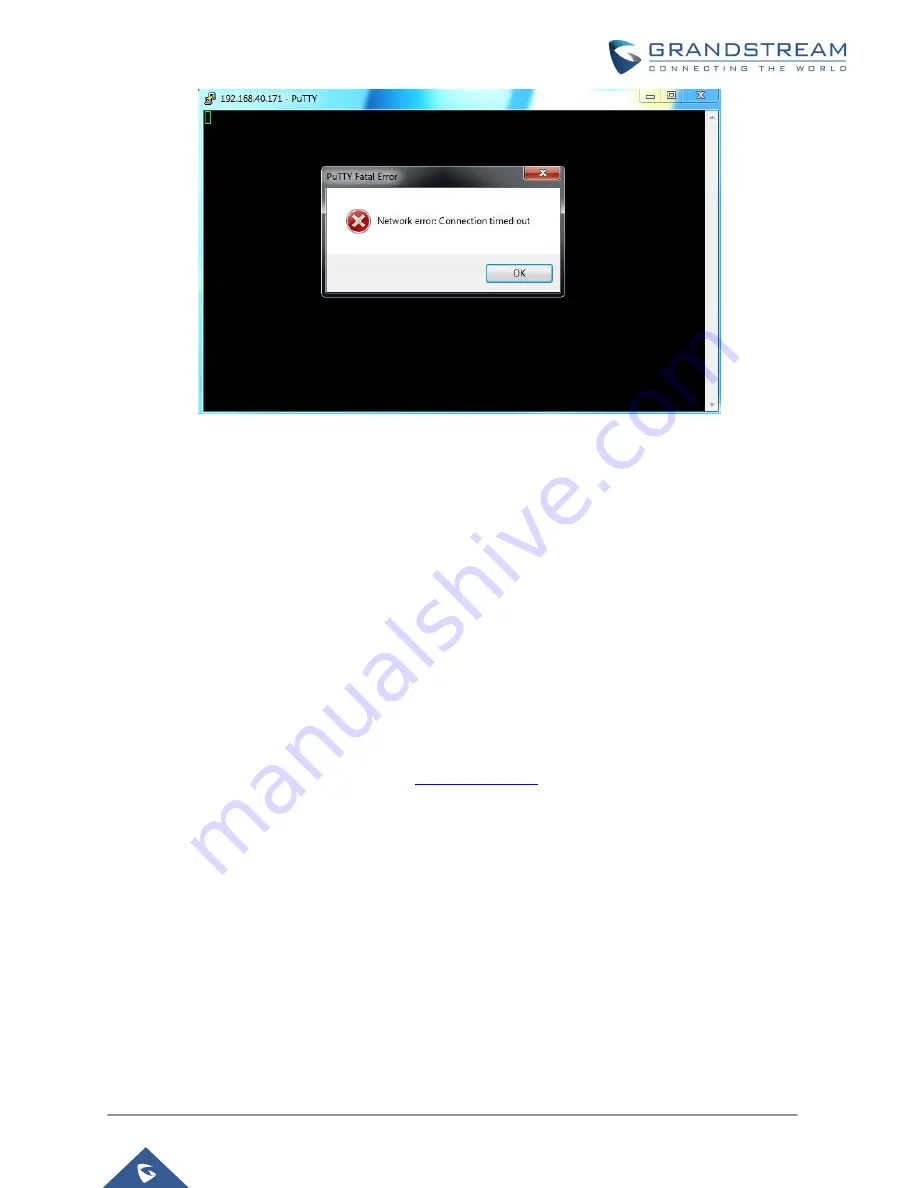
Figure 22: SSH Connection Blocked by UCM
Dynamic Defense
Dynamic defense is supported on UCM6102/UCM6202/UCM6204/UCM6208 and UCM6510 when LAN
mode is set to “Route”. It can be configured from Web UI
System Settings
Security Settings
Dynamic
Defense. Once enabled, it will try to blacklist massive connection attempts or brute force attacks made by
individual host.
The UCM Dynamic Defense model also allows users to customize the connection threshold and time
interval, meaning users can manually set the period for the max connection made by individual IP address.
In addition, whitelist is supported so that certain hosts will not be blocked by Dynamic Defense.
For more configuration details, please refer to
Fail2ban
Fail2Ban is mainly designed to detect and prevent intrusion for authentication errors in SIP REGISTER,
INVITE and SUBSCRIBE method. It can be configured from Web UI
System Settings
Security
Settings
Fail2ban. Users can customize the maximum retry times that one host can attempt in a period of
time. If a host initiates attempts which exceed maximum retry times, it will be banned by UCM for a certain
amount of time. User can also add a whitelist for the host that will not be punished by this defensive
mechanism.
Fail2Ban can be enabled in the UCM web UI
System Settings
Security Settings
Fail2Ban. By default,
Fail2Ban is disabled (see figure below).




































