3.
Click
Modify
.
4.
You can edit the name and the contact information of the user.
5.
The
Imei changes
field is updated every time the user changes the device. The user account is disabled
when the license is used in more than 3 devices, for example, when the user upgrades the mobile device.
Reset the
Imei changes
value to enable the user account so that the user can activate the client application
again.
6.
Click
Save
to accept changes.
Anti-theft management
With Anti-theft, you can make sure that an end-user's device or data stored on it is not misused if the device
is stolen.
With Anti-theft management, you can remotely lock, wipe or reset the Anti-theft settings on an end-user's
device. All Anti-theft operations are logged and shown in the user subscription details view.
Using the remote Anti-theft
You can remotely lock, wipe or reset the Anti-theft settings for an end-user with a subscription that you can
manage.
To remotely run Anti-theft operations, follow these instructions.
1.
To find the end-user information you want to modify, you can use the
Seach
user search to find the
end-user account that you want to modify.
2.
Click the name of the end-user in the search results to view detailed account information.
The user subscription details view opens.
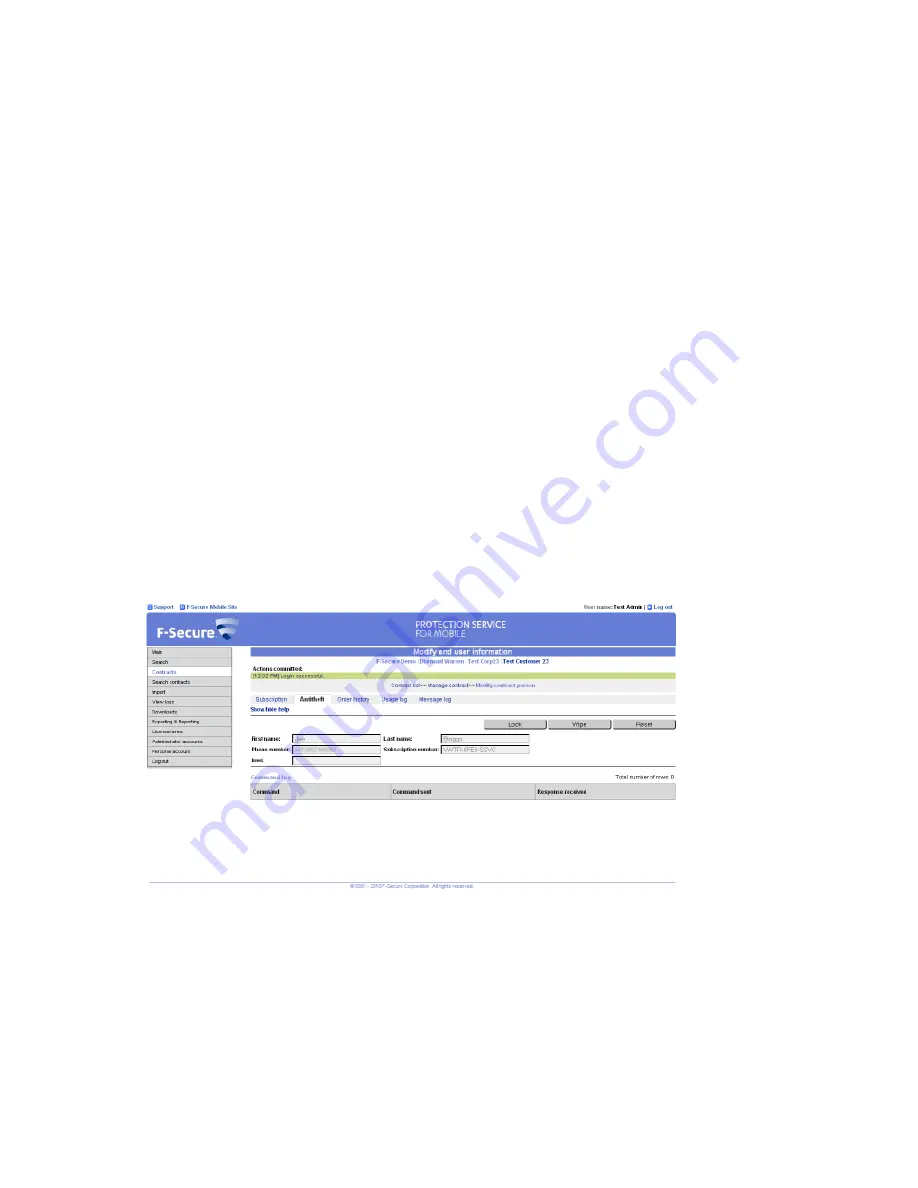
3.
Click
Antitheft
in the menu to view the Anti-theft operation log for the end-user and to run remote operations.
•
To remotely lock the end-user's device, click
Lock
. Once the command is sent, the end-user can unlock
the device by entering the system lock password. If the end-user has not set up the Anti-theft settings,
you can unlock the device by sending a
Reset
command.
•
To remotely erase all data stored on the end-user's device, click
Wipe
.
•
To remotely reset the Anti-theft settings on the end-user's device, click
Reset
.
4.
In the confimation dialog, select the confirmation checkbox and click
OK
.
F-Secure Mobile Security for Business | Using the management portal |
13
Summary of Contents for MOBILE SECURITY FOR BUSINESS -
Page 1: ...F Secure Mobile Security for Business Corporation administrator s guide...
Page 2: ......
Page 4: ...4 F Secure Mobile Security for Business TOC...
Page 22: ......
Page 23: ...F Secure Mobile Security for Business Region administrator s guide...
Page 24: ......
Page 26: ...4 F Secure Mobile Security for Business TOC...
Page 44: ......




























