23
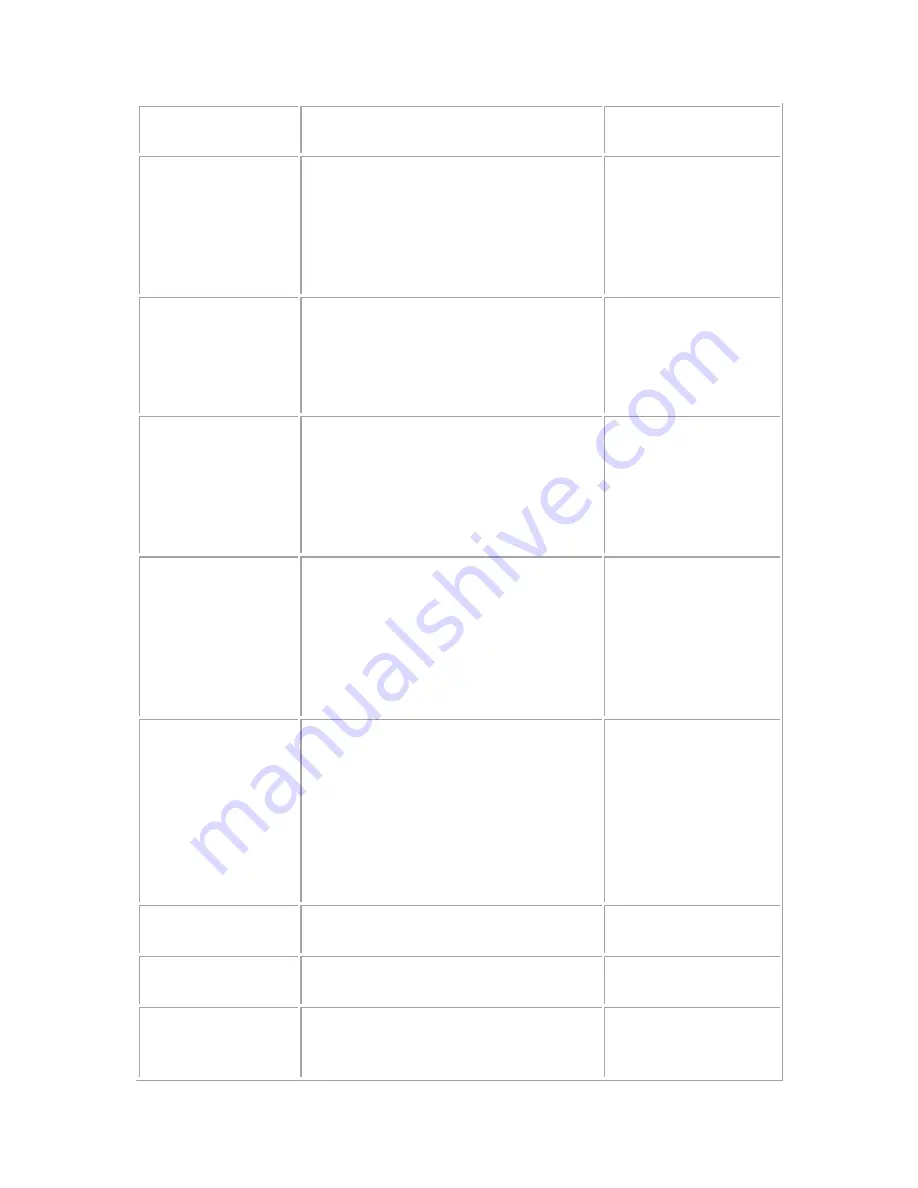
Category
Description
User Configurable
options
SIP
Reconnaissance
Attacks
The intruder is trying to detect what
version of Asterisk you are running.
With that info, he will start exploiting
the numerous vulnerabilities of that
version. The SIP Firewall will not
respond to his query.
N/A
SIP
Devices
Scanning
The intruder will scan the PBX ports to
see what devices are connected to it.
With that info, he can exploit 3rd party
vulnerabilities. The SIP Firewall will not
respond to his query.
N/A
SIP
Extensions
Discovery
The intruder will ask the PBX to
divulge the range of the extension
numbers. With that info, he can try
different passwords to take control of
these extensions. The SIP Firewall will
not respond to that query.
Invalid SIP User
Registration
Attempts/Duration
Multiple
Authentication
Failures/Brute force
password Attempt
The intruder will try to log in with
different user names and passwords
multiple times. Once he succeeds, he
will have control of that extension. The
SIP Firewall can block, log or blacklist
the IP for a period of time if it exceeds
the authorized number of trials/second.
Failed Authentication
Attempts/Duration
Ghost calls Attempt
The intruder will generate calls to an
extension and it will look like the calls
come from that same extension. His
goal is to crash the PBX resulting in
disrupted communication. The SIP
Firewall can block, log or blacklist the
IP for a period of time if it exceeds the
authorized number of trials/second.
No of Anonymous
Invite
Responses/Duration
SIP Dos Attacks
Flooding attempts using various SIP
messages.
No of SIP Request
Messages/Duration
SIP DDos Attacks
Distributed flooding attempts using
various SIP messages.
No of SIP Response
Messages/Duration
SIP
Anomaly
attacks
The intruder will send abnormal SIP
packets to the PBX. His goal is to
crash the PBX resulting in disrupted
N/A
Summary of Contents for SIP Firewall
Page 1: ......
Page 2: ...Elastix SIP Firewall User Manual ...
Page 23: ...21 Figure 15 Logging ...
Page 33: ...31 Figure 25 Geo IP Filters ...






























