17
Table 3-5 Wiegand output
Parameter
Description
Wiegand output type
The
Wiegand
output type determines the card number or the digit of
the number than can be recognized by the standalone.
Wiegand26, three bytes, six digits.
Wiegand34, four bytes, eight digits.
Wiegand66, eight bytes, sixteen digits.
Pulse Width
You can set pulse width and pulse interval.
Pulse Interval
Output Data Type
You can select the types of output data.
User ID: If User ID is selected, and then user ID will be output.
Card No.: If Card No. is selected, and then card number will be
output.
3.8.3 TCP Port
The range is 1025-65535, and it is 37777 by default. If you modify the port, the system will
restart automatically.
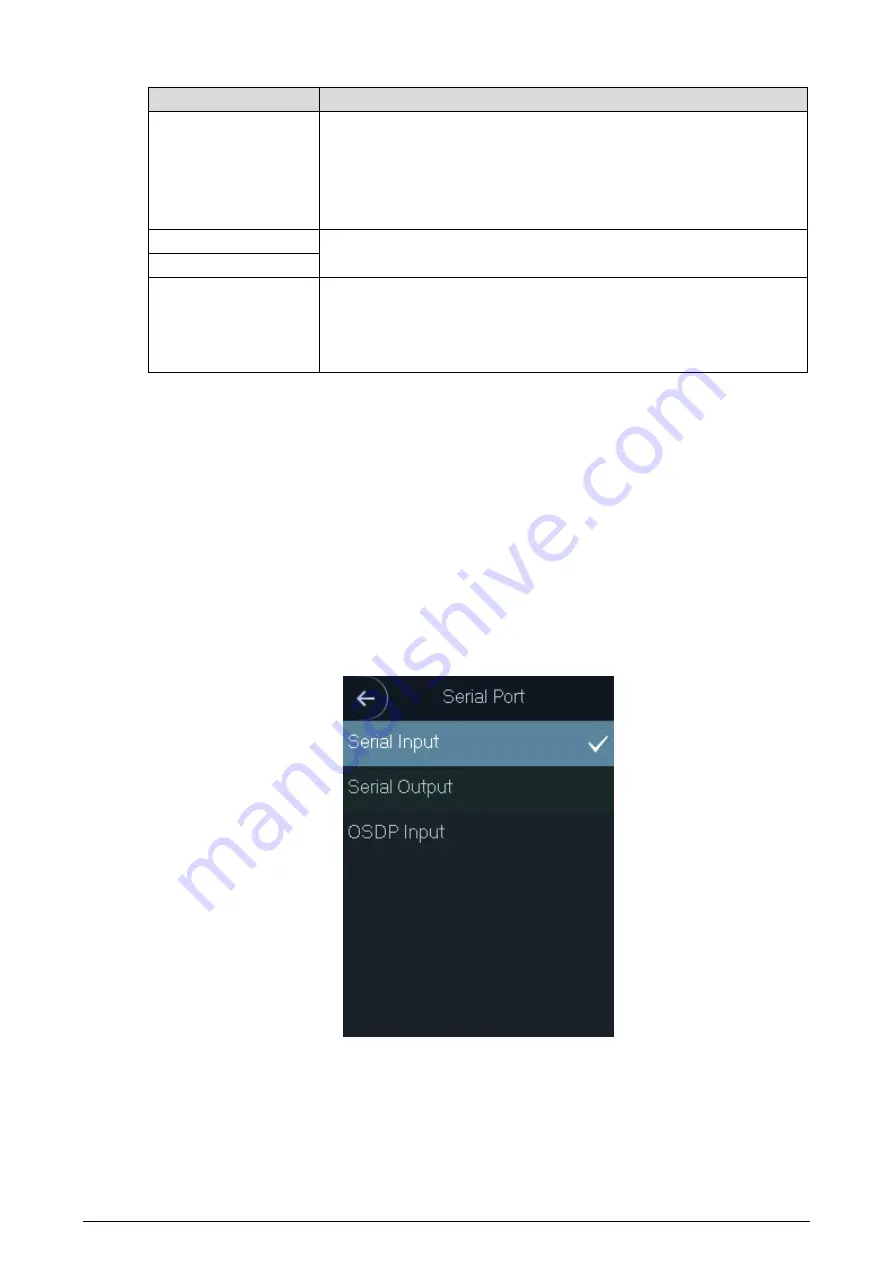
3.8.4 Serial Port Settings
Select serial input or serial output according to the entering direction and exiting direction.
Select
Comm > Serial Port
.
Serial port
Figure 3-11
Select
Serial Input
when external devices that are with card reading and writing functions
are connected to the standalone.
Serial Input
is selected to enable access card
information to be sent to the standalone and the management platform.
For standalones with fingerprint recognition, card reading and writing functions, if you
select
Serial Output
, standalone will send card number or user ID to the controller.
Summary of Contents for Access Standalone
Page 1: ...Access Standalone User s Manual V1 0 1...
Page 55: ...47 The homepage of the web is displayed...
Page 57: ...49 Homepage Figure 6 2 On the homepage click Device Step 4 Device Figure 6 3 Click Add Step 5...
Page 64: ...56 Authentication Figure 6 12 Click Edit and then click in Card section Step 2...
Page 65: ...57 Editing Figure 6 13 Select the card reader of the access standalone as needed Step 3...
Page 71: ...63 User group manager Figure 6 19 2 Click Add...
















































