69
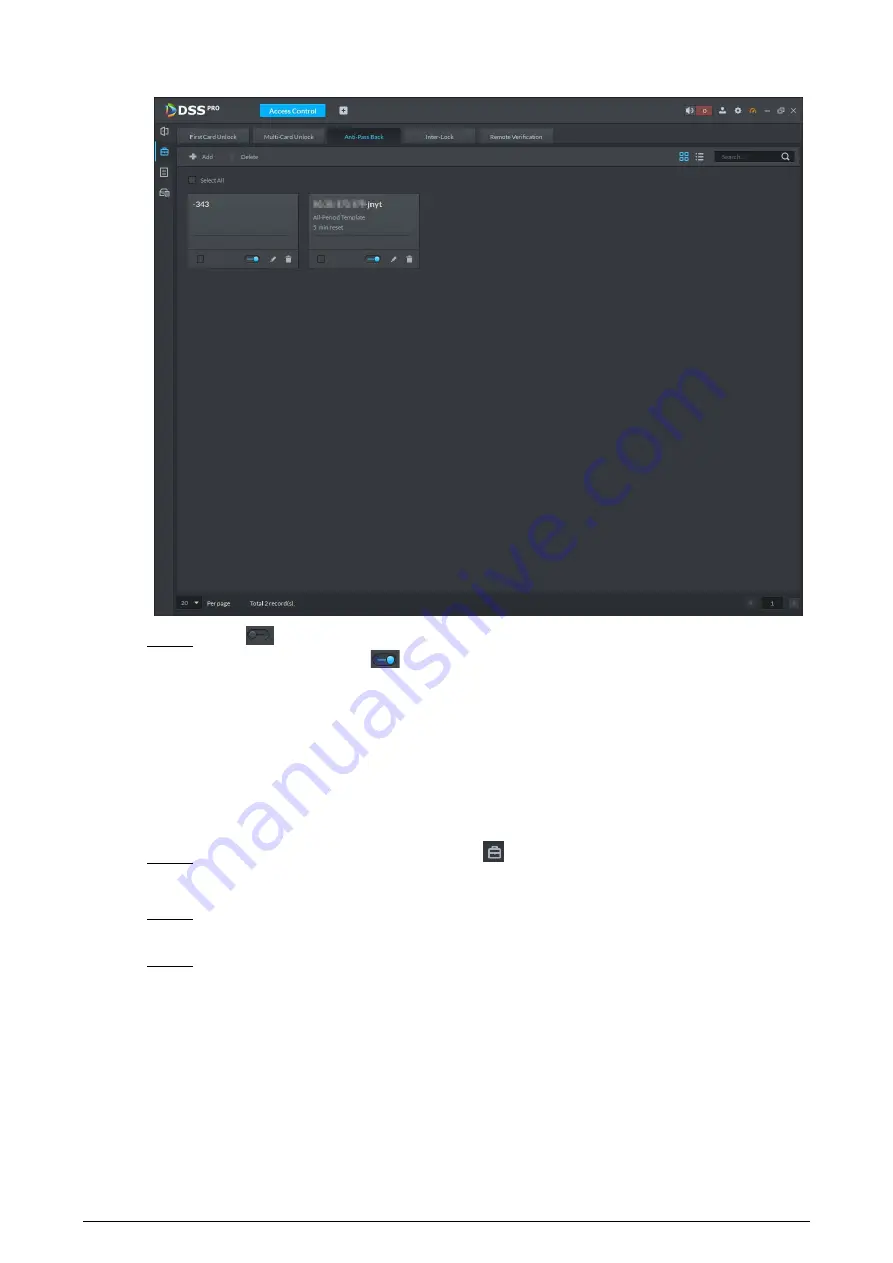
Anti-passback information
Figure 6-25
Click
.
Step 5
The icon changing into
indicates Anti-passback is enabled.
6.2.7 Remote Verification
For devices with remote verification, when users unlock the doors with card, fingerprint, or
password in the specified time period, it must be confirmed on the platform client before the
access controller can be opened.
On the
Access Control
interface, click
.
Step 1
The
Advanced Function
interface is displayed.
Click the
Remote Verification
tab.
Step 2
The
Remote Verification
interface is displayed.
Click
Add
.
Step 3
Summary of Contents for Access Standalone
Page 1: ...Access Standalone User s Manual V1 0 1...
Page 55: ...47 The homepage of the web is displayed...
Page 57: ...49 Homepage Figure 6 2 On the homepage click Device Step 4 Device Figure 6 3 Click Add Step 5...
Page 64: ...56 Authentication Figure 6 12 Click Edit and then click in Card section Step 2...
Page 65: ...57 Editing Figure 6 13 Select the card reader of the access standalone as needed Step 3...
Page 71: ...63 User group manager Figure 6 19 2 Click Add...























