6-18
Firepower 8000 Series Hardware Installation Guide
Chapter 6 Deploying Firepower Managed Devices
Complex Network Deployments
Complex Network Deployments
Your enterprise’s network may require remote access, such as using a VPN, or have multiple entry
points, such as a business partner or banking connection.
Integrating with VPNs
Virtual private networks, or VPNs, use IP tunneling techniques to provide the security of a local network
to remote users over the Internet. In general, VPN solutions encrypt the data payload in an IP packet.
The IP header is unencrypted so that the packet can be transmitted over public networks in much the
same way as any other packet. When the packet arrives at its destination network, the payload is
decrypted and the packet is directed to the proper host.
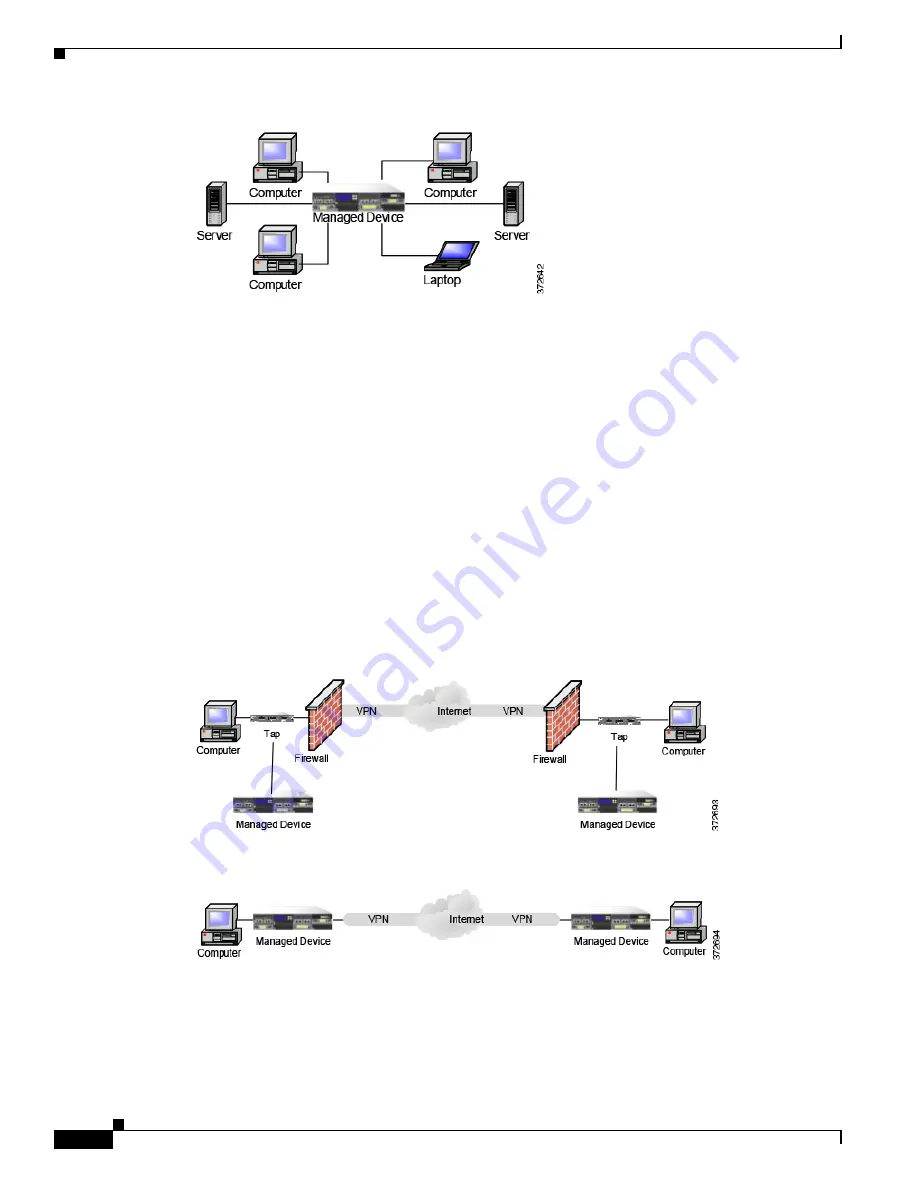
Because network appliances cannot analyze the encrypted payload of a VPN packet, placing managed
devices outside the terminating endpoints of the VPN connections ensures that all packet information
can be accessed. The following diagram illustrates how managed devices can be deployed in a VPN
environment.
You can replace the firewall and the tap on either side of the VPN connection with the managed device.
Note that if you replace the tap with a managed device, you lose the tap packet delivery guarantee.


































