Avaya G250 and G250-BRI Branch Office Media Gateways w/FIPS Non-Proprietary Security Policy
Version 1.2 Wednesday, 14 December, 2005
© 2005 Avaya Inc.
May be reproduced only in its original entirety [without revision]. Page 19 of 23
CID 106595
Key
Ena
b
le FIPS mo
de
Firmware Update
CSPs management
User Management
Module configuration
Reset
Read all st
at
us indicat
ions
Module backup
Restore
Zeroization
IK
E negot
iat
ion
IPSec tra
ffic pro
cessing
Read subset
of
st
at
us
indications
OSPF ro
uting
PPPo
E Serv
ice
Ra
dius Authentica
tio
n
Serial Number Exchange
Ephemeral DH Phase-2
private key
Z Z
RW
Ephemeral DH Phase 2
shared secret
Z Z
RW
User password
WZ R R WZ R R R R R Z R
Root password
RW RW R W R R R R R W* R
OSPF Secret
WZ WZ Z Z R
Radius Secret
WZ WZ
Z R
PPPoE Chap/PAP
Secret
WZ W Z Z R
SNMPv3
authentication
password
WZ R R WZ R R R R R Z
Fixed Serial Number
secret
W
Z
R
Ephemeral Serial
Number secret
Z Z RW
IKE Ephemeral DH
public keys
Z Z
RW
IKE Ephemeral DH
Phase 2 public keys
Z Z
RW
Avaya root CA RSA
public key
RW
License RSA public
key
R
RW
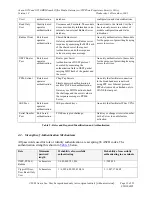
Table 10– CSP Access Rights within Roles & Services
(*) – The root password is set back to a factory default value during zeroization.
6. Operational
Environment
The FIPS 140-2 Area 6 Operational Environment requirements are not applicable because the
device does not support the loading and execution of un-trusted code. Avaya digitally signs
firmware images of the crypto module using RSA. Through this signature, the crypto module
verifies the authenticity of any update to its firmware image.