21
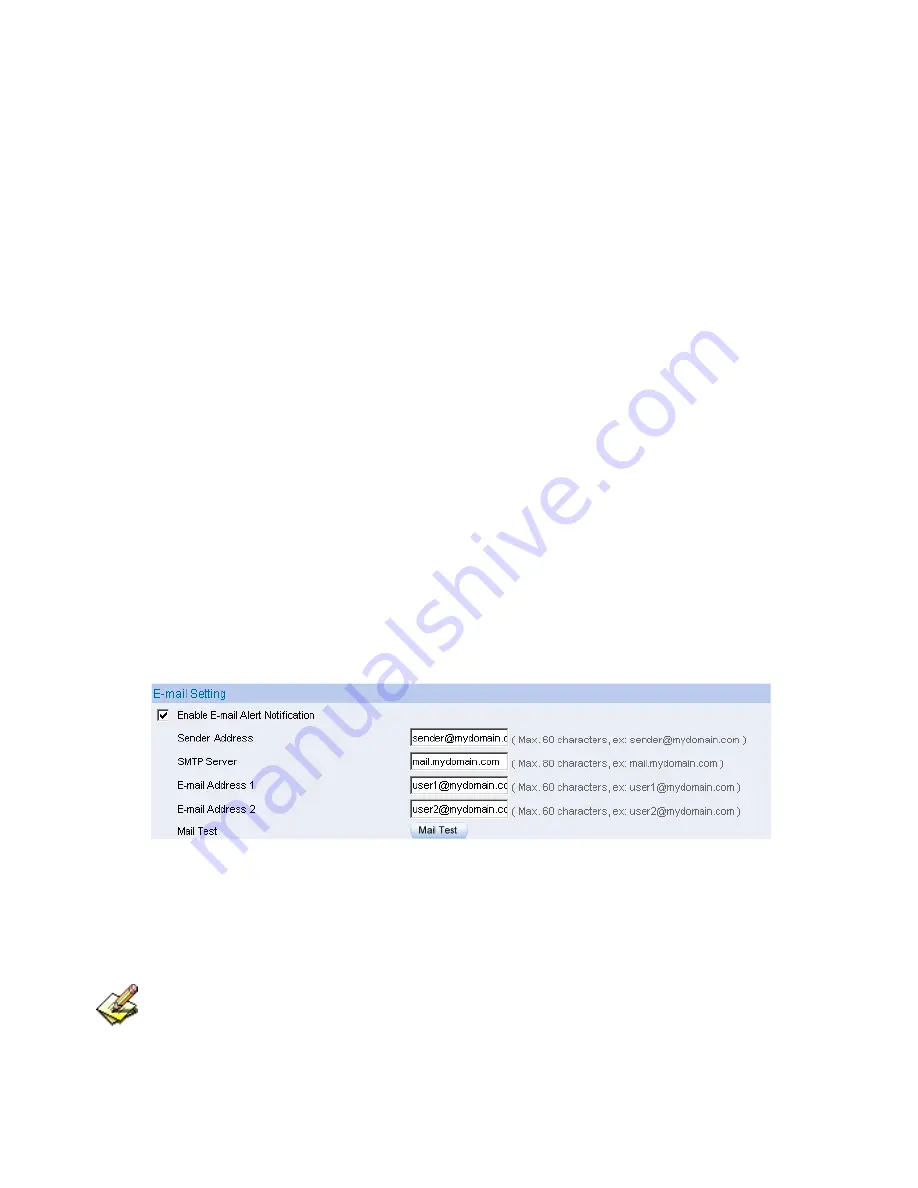
Enabling E-mail Alert Notification
STEP 1
﹒
Select
Enable E-mail Alert Notification
under E-Mail Settings.
STEP 2
﹒
Sender Address:
Enter the Sender Address. (Required by some
ISPs.)
STEP 3
﹒
SMTP Server IP:
Enter SMTP server’s IP address.
STEP 4
﹒
E-Mail Address 1:
Enter the e-mail address of the first user to be
notified.
STEP 5
﹒
E-Mail Address 2:
Enter the e-mail address of the second user to be
notified. (Optional)
STEP 6
﹒
Click
OK
on the bottom-right of the screen to enable E-mail Alert
Notification. (Figure2-5)
Figure2-5 Enable E-mail Alert Notification
Click on
Mail Test
to test if E-mail Address 1 and E-mail Address 2 can receive the
Alert Notification correctly.
Summary of Contents for ALL7008
Page 1: ...ALL7008 User s Manual...
Page 5: ...4 Chapter21 Status 423 Interface 424 Authentication 426 ARP Table 427 DHCP Clients 428...
Page 13: ...12...
Page 36: ...35 STEP 4 Complete PPTP VPN Connection Figure 2 20 Figure 2 20 PPTP VPN Connection Setting...
Page 43: ...42...
Page 55: ...54 Figure3 8 Complete Dynamic IP Connection Setting...
Page 83: ...82...
Page 85: ...84 Figure7 2 the Flow After Using QoS Max Bandwidth 400Kbps Guaranteed Bandwidth 200Kbps...
Page 114: ...113 STEP 10 Select Ethernet Figure8 23 Figure8 23 Add New Remote Access Policy Method...
Page 119: ...118 STEP 15 Add Service Type Figure8 28 Figure8 28 Add New RADIUS Attribute...
Page 145: ...144...
Page 165: ...164...
Page 191: ...190 STEP 8 Click on Next Figure11 39 Figure11 39 Enable IP Security Policy...
Page 260: ...259 STEP 4 Complete PPTP VPN Connection Figure11 128 Figure11 128 PPTP VPN Connection Setting...
Page 274: ...273 Figure11 142 PPTP VPN Connection Complete...
Page 301: ...300...
Page 343: ...342 Figure14 34 Create Folder WebUI...
Page 345: ...344 Figure14 36 Select Folder for Spam Mail to move to...
Page 347: ...346 Figure14 38 Compact SpamMail Folder...
Page 349: ...348 Figure14 40 Copy the File Address that SpamMail File Store...
Page 353: ...352 Figure14 43 Confirm that All of the Mail in SpamMail File had been Deleted...
Page 355: ...354 Figure14 45 Create Folder Function WebUI...
Page 357: ...356 Figure14 47 Select the Folder for Needed Spam Mail to Move to...
Page 359: ...358 Figure14 49 Compact HamMail File...
Page 361: ...360 Figure14 51 Copy the File Address that HamMail File Store...
Page 364: ...363 Figure14 54 Make Sure all of the Mails in HamMail File had been Deleted...
Page 365: ...364...
Page 381: ...380...
Page 389: ...388 Figure16 4 NetBIOS Alert Notification to Administrator s PC...
Page 390: ...389 Figure16 5 E mail Virus Alert...
Page 391: ...390...
Page 397: ...396...
Page 413: ...412...
Page 417: ...416...
Page 426: ...425 Figure21 1 Interface Status...
Page 430: ...429...
















































