EKI-6333AC-2GD Series User Manual
53
3.5.3.2
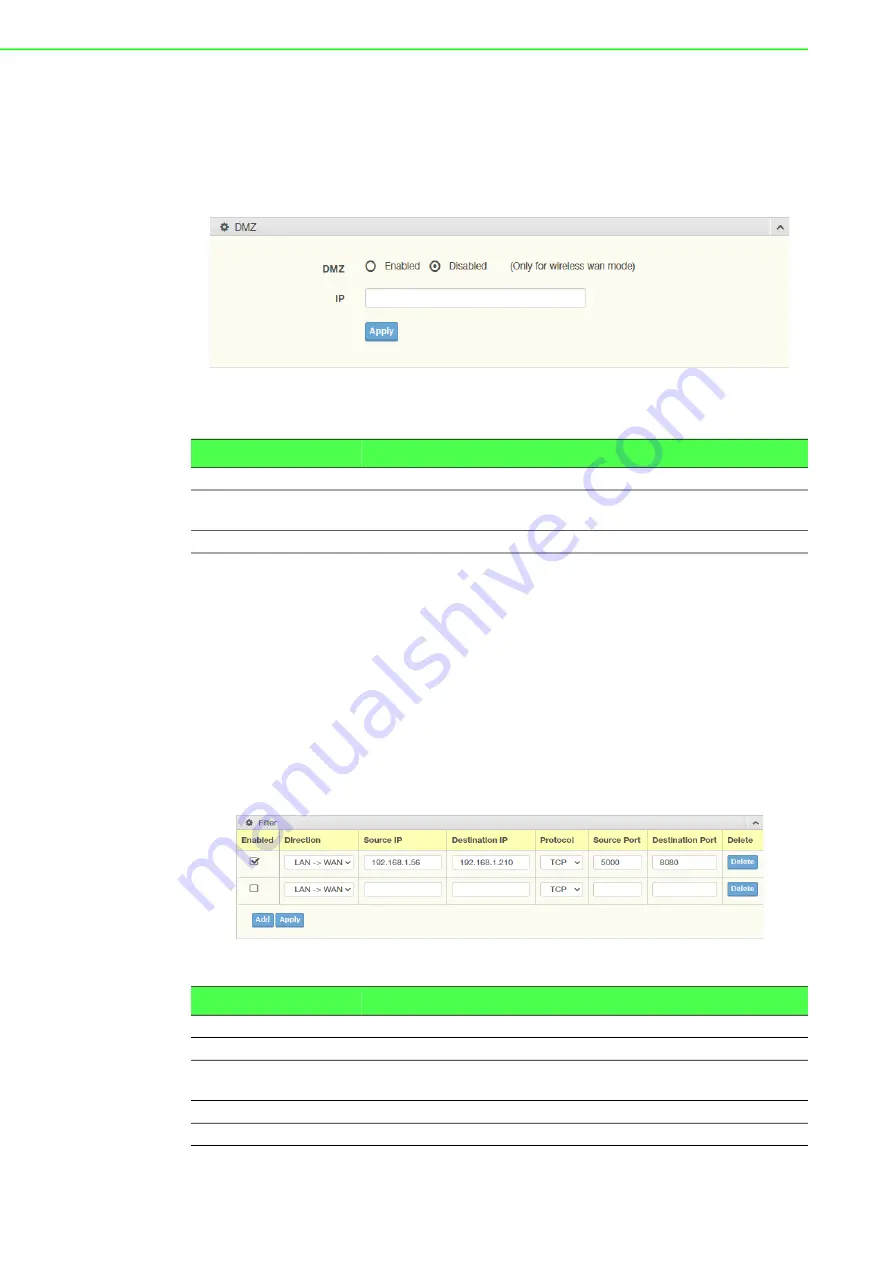
DMZ
A Demilitarized Zone is used to provide Internet services without sacrificing
unauthorized access to its local private network. Typically, the DMZ host contains
devices accessible to the Internet traffic, such as Web (HTTP) servers, FTP servers,
SMTP (e-mail) servers and DNS servers.
To access this page, click
Networking
>
Forwarding
>
DMZ
.
Figure 3.46 Networking
>
Forwarding
>
DMZ
The following table describes the items in the previous figure.
3.5.4
Security
3.5.4.1
Filter
The firewall is a system or group of systems that enforce an access control policy
between two networks. It may also be defined as a mechanism used to protect a
trusted network from an un-trusted network. The device supports Source IP Filtering,
Destination IP Filtering, Source Port Filtering, and Destination Port Filtering.
Source IP Filtering: The source IP filtering gives users the ability to restrict certain
types of data packets from users local network to Internet through the device. Use of
such filters can be helpful in securing or restricting users local network.
To access this page, click
Networking >
Security
>
Filter
.
Figure 3.47 Networking
>
Security
>
Filter
Item
Description
DMZ
Click the radio button to enable or disable the DMZ function.
IP
Enter the IP address to designate a static IP address as the DMZ
target.
Submit
Click
Submit
to save the values and update the screen.
Item
Description
Filter
Click the radio button to enable or disable the Filter policy.
Enabled
Select to enable the defined filter entry.
Direction
Click the drop-down menu to select the direction of the data packet
taffic for the entry: LAN to WAN, WAN to LAN.
Source IP
Enter the IP address of the sender address.
Destination IP
Enter the IP address of the destination address.
























