C
HAPTER
2: D
RILL
D
OWN
INTO
A
URL G
AUGE
S
TEP
1: H
OW
TO
R
EAD
A
G
AUGE
4
8
E
6 T
ECHNOLOGIES
, T
HREAT
A
NALYSIS
R
EPORTER
E
VALUATION
G
UIDE
C
HAPTER
2: D
RILL
D
OWN
INTO
A
URL G
AUGE
This section will step you through the manual monitoring of users in real-time via
the URL gauge dashboard. Note that this is simply one of many ways to use TAR
to monitor insider threats. There is also a robust automated alert component that
does not require the system administrator to be monitoring gauges in order to be
notified of a violation in process.
Step 1: How to Read a Gauge
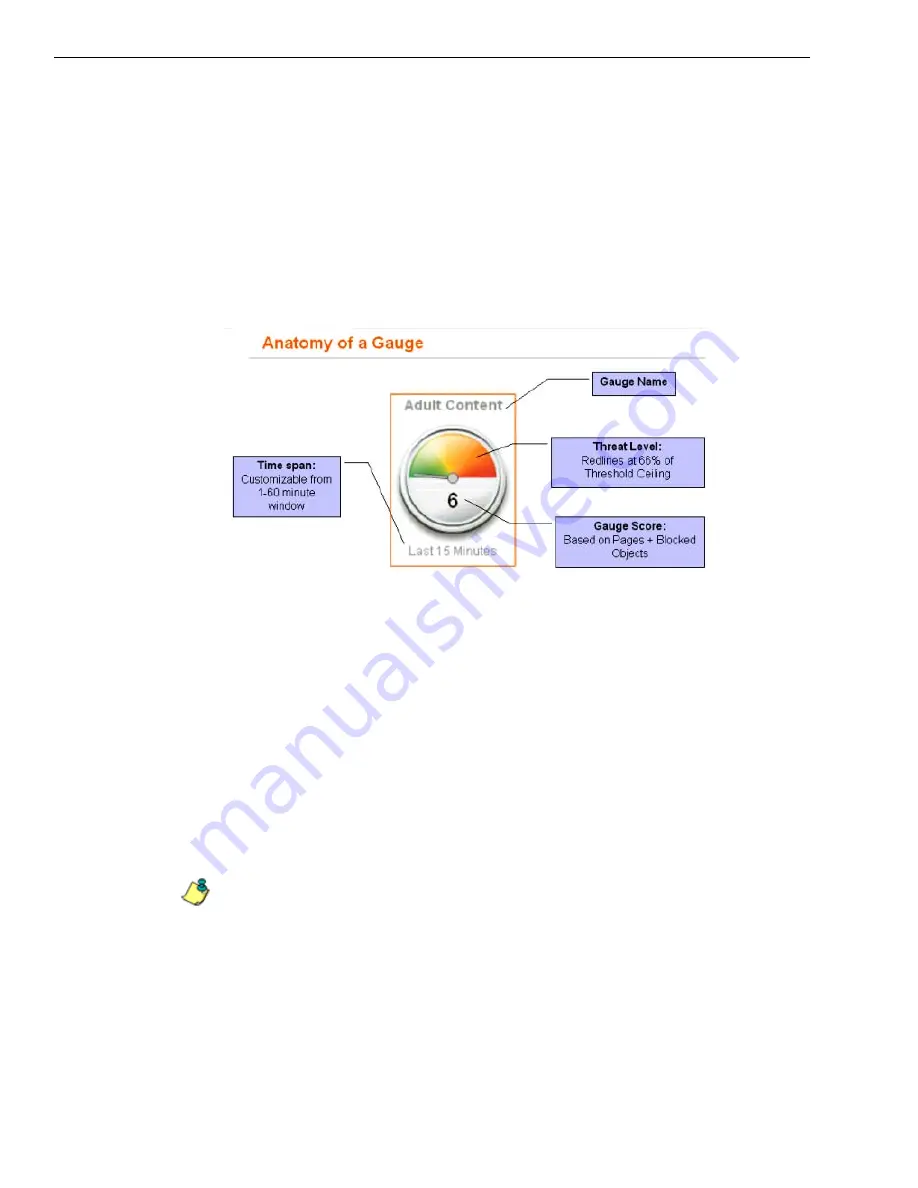
The graphic below describes how to read gauges on the URL dashboard:
Anatomy of a gauge diagram
Gauge Name
The gauge name is the customized name of the gauge created by the adminis-
trator. TAR has five default sample gauges that correspond with five of 8e6’s
super-categories: Adult Content, Security, Shopping, Bandwidth and Illegal.
Administrators can create their own gauges as well as delete the default gauges.
Score
The score is the large number in the center of the gauge that is based upon the
number of URL page hits (see NOTE below) that occur in this specific category in
a given period of time.
NOTES
: In addition to page hits, TAR also counts “blocked object” hits. For reference,
“pages hits” are files that typically end in .html and represent a main page view. “Object
hits” are files that typically end in .gif or .jpg and represent image files.
To streamline your task, TAR does not track a score for “non-blocked objects,” since these
gauges are designed to provide a clear picture of how many times a user has requested a
page, and objects are images hosted within a page. TAR includes blocked object data to
cover instances in which harmful images are hosted on a non-harmful site.








































