ZyWALL 5 User’s Guide
Chapter 9 Firewalls
155
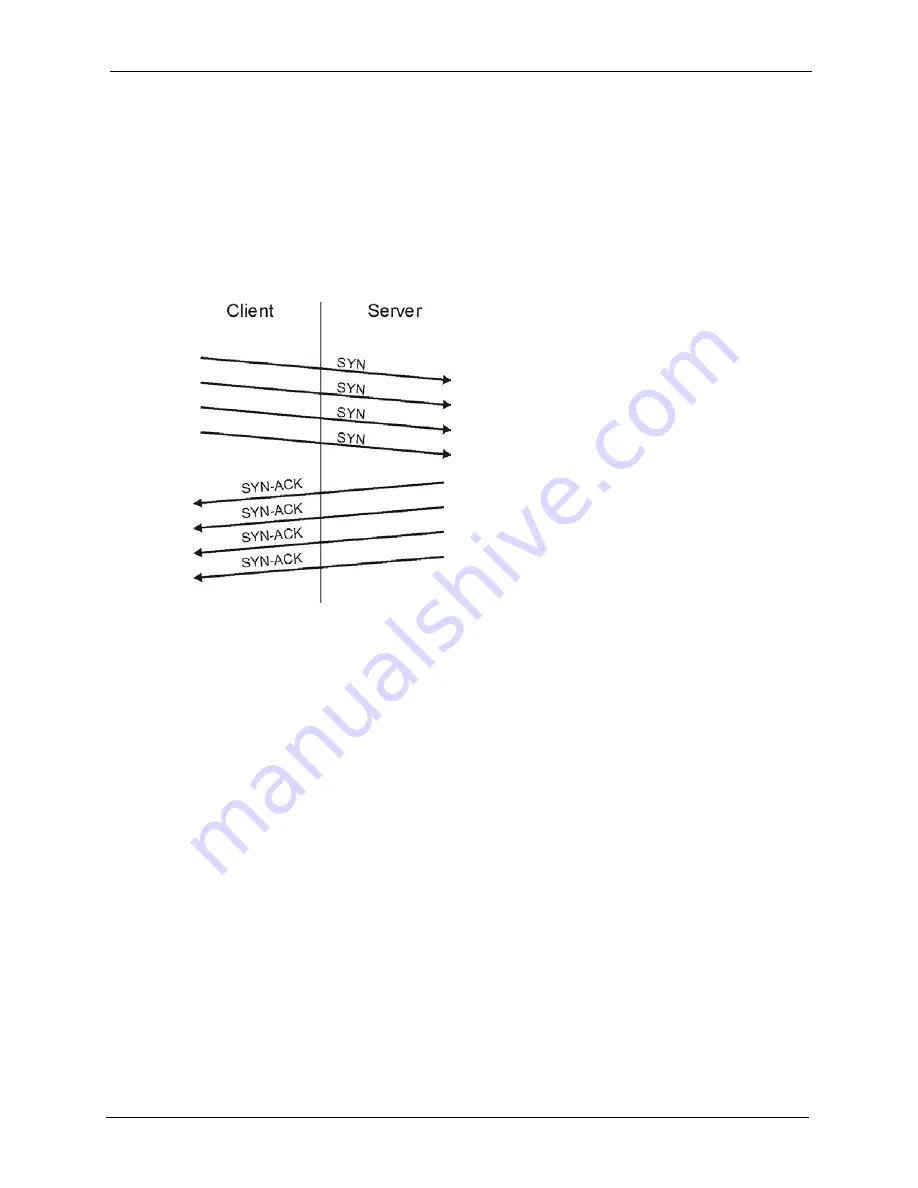
response. While the targeted system waits for the ACK that follows
the SYN-ACK, it queues up all outstanding SYN-ACK responses on
what is known as a backlog queue. SYN-ACKs are moved off the
queue only when an ACK comes back or when an internal timer
(which is set at relatively long intervals) terminates the three-way
handshake. Once the queue is full, the system will ignore all
incoming SYN requests, making the system unavailable for
legitimate users.
Figure 60
SYN Flood
b
In a
LAND Attack
, hackers flood SYN packets into the network with
a spoofed source IP address of the targeted system. This makes it
appear as if the host computer sent the packets to itself, making the
system unavailable while the target system tries to respond to itself.
• A
brute-force
attack, such as a "Smurf" attack, targets a feature in the IP specification
known as directed or subnet broadcasting, to quickly flood the target network with
useless data. A Smurf hacker floods a router with Internet Control Message Protocol
(ICMP) echo request packets (pings). Since the destination IP address of each packet is
the broadcast address of the network, the router will broadcast the ICMP echo request
packet to all hosts on the network. If there are numerous hosts, this will create a large
amount of ICMP echo request and response traffic. If a hacker chooses to spoof the
source IP address of the ICMP echo request packet, the resulting ICMP traffic will not
only clog up the "intermediary" network, but will also congest the network of the spoofed
source IP address, known as the "victim" network. This flood of broadcast traffic
consumes all available bandwidth, making communications impossible.
Содержание ZyXEL ZyWALL 5
Страница 1: ...ZyWALL 5 Internet Security Appliance User s Guide Version 3 64 3 2005 ...
Страница 2: ......
Страница 26: ...ZyWALL 5 User s Guide 24 ...
Страница 44: ...ZyWALL 5 User s Guide 42 ...
Страница 86: ...ZyWALL 5 User s Guide 84 Chapter 3 Wizard Setup ...
Страница 96: ...ZyWALL 5 User s Guide 94 Chapter 4 LAN Screens ...
Страница 102: ...ZyWALL 5 User s Guide 100 Chapter 5 Bridge Screens ...
Страница 130: ...ZyWALL 5 User s Guide 128 Chapter 7 WAN Screens Figure 45 WAN PPPoE Encapsulation ...
Страница 138: ...ZyWALL 5 User s Guide 136 Chapter 7 WAN Screens Figure 50 Dial Backup Setup ...
Страница 144: ...ZyWALL 5 User s Guide 142 Chapter 7 WAN Screens ...
Страница 152: ...ZyWALL 5 User s Guide 150 Chapter 8 DMZ Screens ...
Страница 174: ...ZyWALL 5 User s Guide 172 Chapter 10 Firewall Screens Figure 68 Creating Editing A Firewall Rule ...
Страница 179: ...ZyWALL 5 User s Guide Chapter 10 Firewall Screens 177 Figure 73 My Service Rule Configuration ...
Страница 220: ...ZyWALL 5 User s Guide 218 Chapter 13 Introduction to IPSec ...
Страница 238: ...ZyWALL 5 User s Guide 236 Chapter 14 VPN Screens Figure 110 VPN Rules IKE Network Policy Edit ...
Страница 261: ...ZyWALL 5 User s Guide Chapter 15 Certificates 259 Figure 122 My Certificate Details ...
Страница 280: ...ZyWALL 5 User s Guide 278 Chapter 16 Authentication Server Figure 133 Local User Database ...
Страница 317: ...ZyWALL 5 User s Guide Chapter 19 Bandwidth Management 315 ...
Страница 318: ...ZyWALL 5 User s Guide 316 Chapter 19 Bandwidth Management ...
Страница 352: ...ZyWALL 5 User s Guide 350 Chapter 21 Remote Management ...
Страница 366: ...ZyWALL 5 User s Guide 364 Chapter 23 Logs Screens Figure 188 Log Settings ...
Страница 389: ...ZyWALL 5 User s Guide Chapter 24 Maintenance 387 Figure 210 Restart Screen ...
Страница 390: ...ZyWALL 5 User s Guide 388 Chapter 24 Maintenance ...
Страница 416: ...ZyWALL 5 User s Guide 414 Chapter 27 WAN and Dial Backup Setup ...
Страница 432: ...ZyWALL 5 User s Guide 430 Chapter 30 DMZ Setup ...
Страница 492: ...ZyWALL 5 User s Guide 490 Chapter 37 System Information Diagnosis ...
Страница 508: ...ZyWALL 5 User s Guide 506 Chapter 38 Firmware and Configuration File Maintenance ...
Страница 520: ...ZyWALL 5 User s Guide 518 Chapter 40 Remote Management ...
Страница 536: ...ZyWALL 5 User s Guide 534 Chapter 42 Troubleshooting Figure 343 Java Sun ...
Страница 564: ...ZyWALL 5 User s Guide 562 Appendix C IP Subnetting ...
Страница 570: ...ZyWALL 5 User s Guide 568 Appendix E PPTP ...
Страница 571: ...ZyWALL 5 User s Guide 569 ...
Страница 572: ...ZyWALL 5 User s Guide 570 ...
Страница 590: ...ZyWALL 5 User s Guide 588 Appendix G Triangle Route ...
Страница 620: ...ZyWALL 5 User s Guide 618 Appendix J Importing Certificates ...
Страница 622: ...ZyWALL 5 User s Guide 620 Appendix K Command Interpreter ...
Страница 628: ...ZyWALL 5 User s Guide 626 Appendix L Firewall Commands ...
Страница 632: ...ZyWALL 5 User s Guide 630 Appendix M NetBIOS Filter Commands ...
Страница 638: ...ZyWALL 5 User s Guide 636 Appendix O Brute Force Password Guessing Protection ...
Страница 660: ...ZyWALL 5 User s Guide 658 Appendix Q Log Descriptions ...