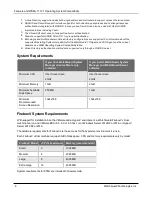
Important Information about Firebox Certificates
SHA-1 is being deprecated by many popular web browsers, and WatchGuard recommends that you now use
SHA-256 certificates. Because of this, we have upgraded our default Firebox certificates. Starting with
Fireware v11.10.4, all newly generated default Firebox certificates use a 2048-bit key length. In addition, newly
generated default Proxy Server and Proxy Authority certificates use SHA-256 for their signature hash
algorithm. Starting with Fireware v11.10.5, all newly generated default Firebox certificates use SHA-256 for
their signature hash algorithm. New CSRs created from the Firebox also use SHA-256 for their signature hash
algorithm.
Default certificates are not automatically upgraded after you install Fireware v11.10.5 or later releases.
To regenerate any default Firebox certificates, delete the certificate and reboot the Firebox. If you want to
regenerate default certificates without a reboot, you can use the CLI commands described in the next section.
Before you regenerate the Proxy Server or Proxy Authority certification, there are some important things to
know.
The Proxy Server certificate is used for inbound HTTPS with content inspection and SMTP with TLS
inspection. The Proxy Authority certificate is used for outbound HTTPS with content inspection. The two
certificates are linked because the default Proxy Server certificate is signed by the default Proxy Authority
certificate. If you use the CLI to regenerate these certificates, after you upgrade, you must redistribute the new
Proxy Authority certificate to your clients or users will receive web browser warnings when they browse
HTTPS sites, if content inspection is enabled.
Also, if you use a third-party Proxy Server or Proxy Authority certificate:
l
The CLI command will not work unless you first delete either the Proxy Server or Proxy Authority
certificate. The CLI command will regenerate both the Proxy Server and Proxy Authority default
certificates.
l
If you originally used a third-party tool to create the CSR, you can simply re-import your existing third-
party certificate and private key.
l
If you originally created your CSR from the Firebox, you must create a new CSR to be signed, and then
import a new third-party certificate.
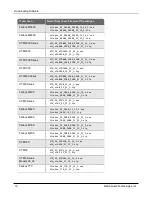
CLI Commands to Regenerate Default Firebox Certificates
To regenerate any default Firebox certificates, delete the certificate and reboot the Firebox. If you want to
regenerate default certificates without a reboot, you can use these CLI commands:
l
To upgrade the default Proxy Authority and Proxy Server certificates for use with HTTPS content
inspection, you can use the CLI command:
upgrade certificate proxy
l
To upgrade the Firebox web server certificate, use the CLI command:
upgrade certificate web
l
To upgrade the SSLVPN certificate, use the CLI command:
upgrade certificate sslvpn
l
To upgrade the 802.1x certificate, use the CLI command:
upgrade certificate 8021x
For more information about the CLI, see the
Command Line Interface Reference
.
Important Information about Firebox Certificates
2
WatchGuard Technologies, Inc.
Содержание Firebox 1500
Страница 24: ...Technical Assistance Release Notes 24...