USR-G808 User Manual
Technical Support:
Jinan USR IOT Technology Limited
www.usriot.com
37
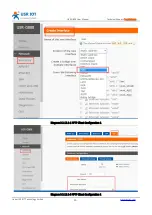
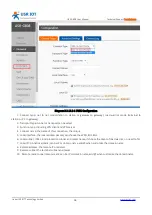
Diagram 3.2.12.2-2 L2TP Client configuration 2
Note:
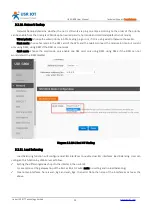
Subnet and LCP setting way can setting according to the notice
When you choose the L2TP OVER IPSEC encryption, the IPSEC configuring can refer the IPSEC.
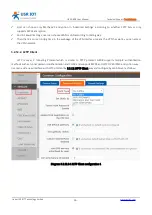
3.2.12.3. IPSEC
IPSEC protocol isn’t a separate protocol. It gives a complete architecture of network data security on the IP layer
and application layer which includes Network Authentication Protocol AH, ESP, IKE and some algorithms for network
authentication/encryption. AH protocol and ESP protocol are used to provide security service, IKE protocol is used to
key exchange.
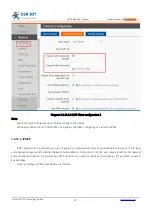
User can configure IPSEC by Web Server as follow: