Authentication and its Application
16
2
Enabling Authentication
To control administrators’ and users’ access to the machine, perform administra-
tor or user authentication using login user names and passwords. To perform
authentication, the authentication function must be enabled. To specify authen-
tication, you need to register administrators.
Reference
For details, see p.20 “Registering the Administrator”.
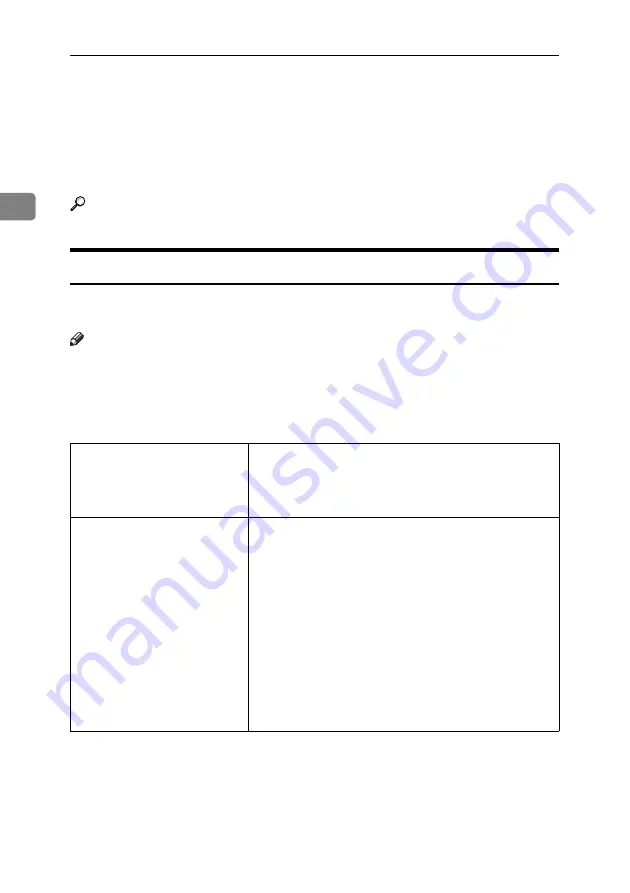
Authentication Setting Procedure
Specify administrator authentication and user authentication according to the
following chart:
Note
❒
To specify Basic Authentication, Windows Authentication, LDAP Authenti-
cation, or Integration Server Authentication, you must first specify adminis-
trator authentication.
❒
You can specify User Code Authentication without specifying administrator
authentication.
Administrator Authentication
See p.17 “Specifying Administra-
tor Privileges”.
Specifying Administrator Privileges
See p.17 “Specifying Administrator Privileges”.
Registering the Administrator
See p.20 “Registering the Administrator”.
User Authentication
See p.16 “Enabling Authentica-
tion”.
Specifying User Authentication
A
Authentication that requires only the machine:
• User Code Authentication
See p.29 “User Code Authentication”.
• Basic Authentication
See p.33 “Basic Authentication”.
B
Authentication that requires external devices:
• Windows Authentication
See p.42 “Windows Authentication”.
• LDAP Authentication
See p.50 “LDAP Authentication”.
• Integration Server Authentication
See p.57 “Integration Server Authentication”.
Содержание Aficio MP C2000
Страница 10: ...2 ...
Страница 80: ...Authentication and its Application 72 2 ...
Страница 108: ...Preventing Information Leaks 100 3 D Press Unlock Files E Press Yes F Press OK ...
Страница 158: ...Enhanced Network Security 150 5 ...
Страница 172: ...Specifying the Extended Security Functions 164 6 ...






























