3. Click the Configure button.
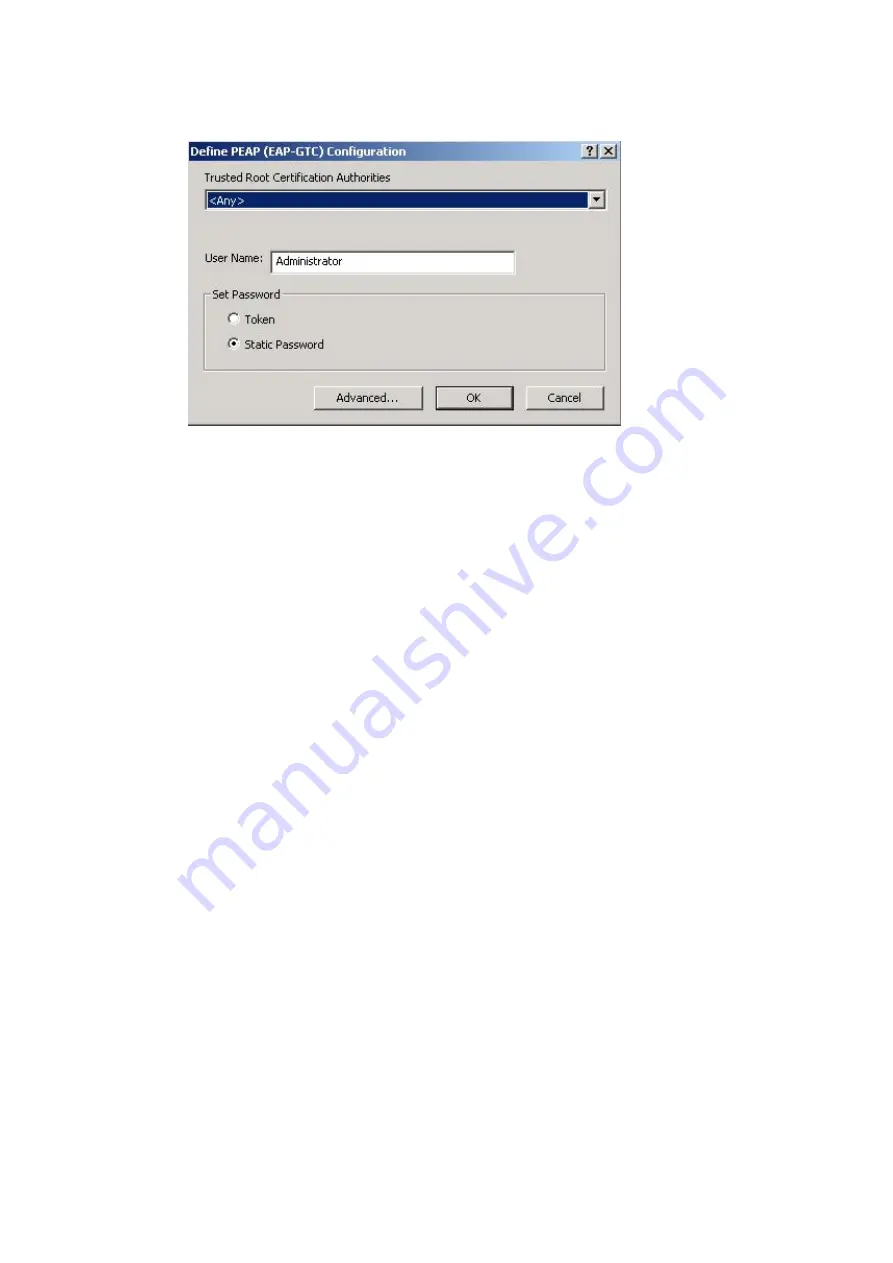
4. Select the appropriate network certificate authority from the drop-down list.
5.
Enter a PEAP user name in the User Name field to use a separate user name and start the
PEAP authentication process.
6. Choose Token or Static Password, depending on the user database.
Note that Token uses a hardware token device or the Secure Computing SofToken program
(version 1.3 or later) to obtain and enter a one-time password during authentication.
7. Click
Advanced
and:
o
Leave the server name field blank for the client to accept a certificate from any server
with a certificate signed by the authority listed in the Network Certificate Authority
drop-down list.
(recommended)
o
Enter the domain name of the server from which the client will accept a certificate.
o
The login name used for PEAP tunnel authentication, fills in automatically as
PEAP-xxxxxxxxxxxx, where xxxxxxxxxxxx is the computer's MAC address. Change
the login name if needed.
8. Click
OK.
9. Enable the profile.
Using PEAP-MSCHAP V2 Security
To use PEAP (EAP-MSCHAP V2) security, the server must have WPA-PEAP certificates, and the
server properties must already be set. Check with the IT manager.
1.
On the Security tab, choose the WPA radio button.
OR: On the Security tab, choose the 802.1x radio button.
2.
Choose PEAP (EAP-MSCHAP V2) from the drop-down menu.
19



























