Wireless Router
User Manual
18
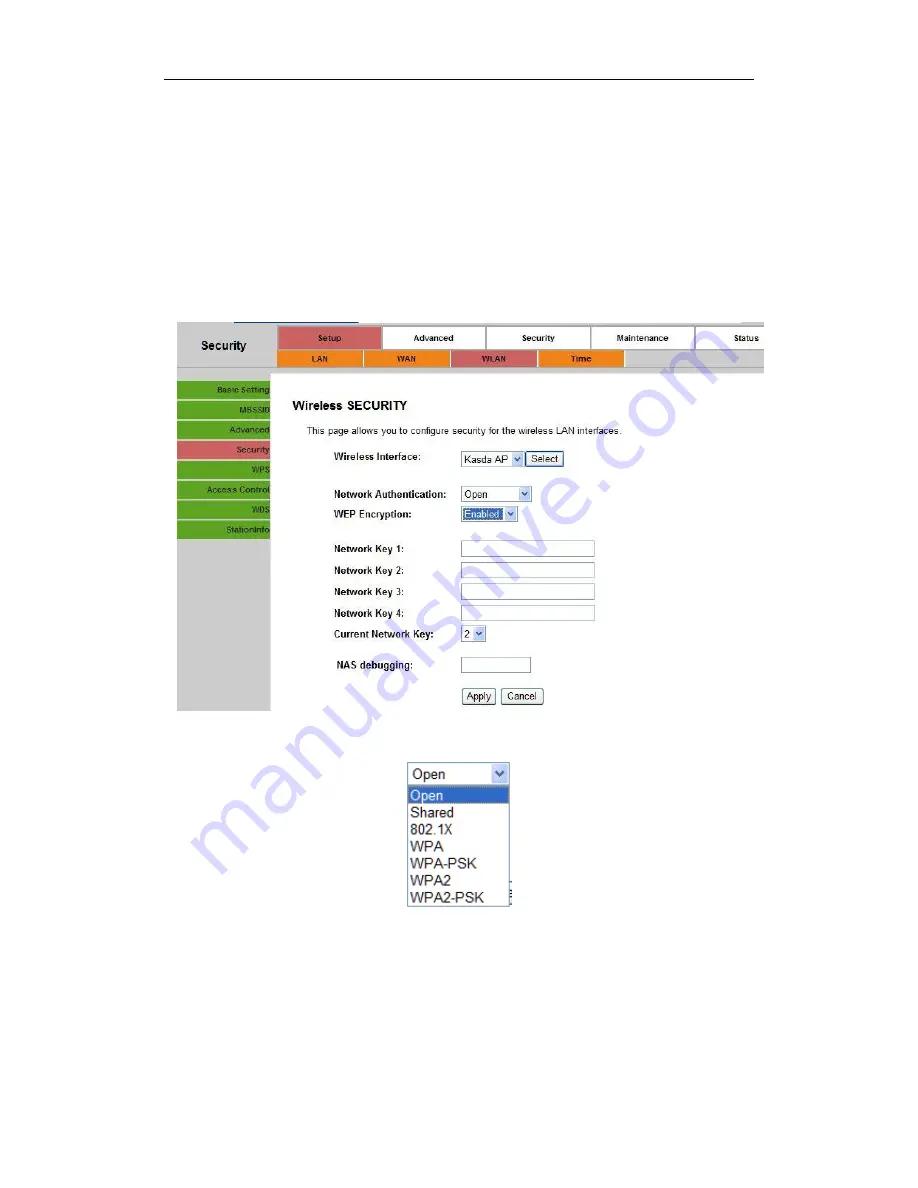
3. To configure security features for the Wireless interface, please open Security item
from Wireless menu. This web page offers nine authentication protocols for user to
secure user’s data while connecting to networks. There are four selections including
Open, Shared, 802.1X,WPA, WPA-PSK, WPA2, WPA2-PSK, Mixed WPA-WPA2,
Mixed WPA-WPA2-PSK. Different item leads different web page settings. Please read
the following information carefully.
The wireless security page allows user to configure the security features of user’s
wireless network.
There are sever
al security methods to choose from, depending on user’s needs
and the capabilities of user’s wireless machines.
WEP open
and
WEP shared
—WEP is an encryption scheme that is used
to protect user’s wireless data communications. WEP uses a combination
of 64-bit keys or 128-
bit keys to provide access control to user’s network
and encryption security for every data transmission. To decode a data
transmission, each wireless client on the network must use an identical
64-bit or 128-bit key. WEP is an older wireless encryption method that is
not as hard to break as the more-recent WPA.
Содержание KW5522H
Страница 1: ...KW5522H Wireless Router User Manual...






































