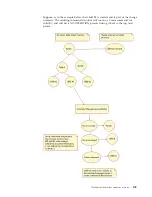
Application sign-on
The Adapter Foundation Classes can use either container-managed or
component-managed authentication or sign-on.
The process of connecting to a back-end application, such an EIS, usually requires
some type of authentication. In a JCA environment, application authentication is
known as
sign-on
. It can be performed in one of two ways:
v
When using container-managed sign-on, the JCA container is responsible for
providing sign-on credentials. Sign-on credentials are passed from the JCA
container to the resource adapter as an instance of
javax.security.auth.Subject
.
v
When using component-Managed sign-on, the adapter client performs a
programmatic sign-on by passing explicit security information, such as
username
and
password
, to the resource adapter using the CCI ConnectionSpec
implementation.
The
res-auth
element in the application component deployment descriptor specifies
the sign-on method. The only valid values for this element are
Container
or
Application
.
Certain back-end systems support reauthentication. Reauthentication is the process
of changing the security context of an existing physical connection. If
reauthentication is supported by the back-end application, you can set the
reauthentication-support
element of the resource adapter deployment descriptor to
true
. Otherwise it must be set to
false
.
Although it does not define a specific authentication mechanism, the JCA
architecture supports two commonly used mechanisms: BasePassword
authentication and Kerberos authentication. Use the
authentication-mechanism-type
element of the resource adapter deployment descriptor to specify which type is
supported.
To support authentication, resource adapters extend
WBIManagedConnection
as
follows:
1.
Implement method
WBIConnection(PasswordCredential pc, boolean
reauthenticate)
.
2.
Extract and use the credentials provided in the
PasswordCredential
instance
that is passed; the Foundation Classes provide values from either the subject
for container-managed sign-on or a
WBIConnectionSpec
instance for
component-managed sign-on as appropriate.
3.
(If you don’t support reauthentication, skip this step.) Check if the
reauthentication flag is true and reset the connection authentication
appropriately; this flag should be set to true only if the developer updates the
deployment descriptor.
4.
Return a
WBIConnection
instance.
5.
(Optionally) override
isConnectionInfoOverwriteable(
). This value is used to
determine whether the
WBIConnectionRequestInfo
already associated with the
ManagedConnection
can be overwritten by another parameter that satisfies the
match condition. By default, this method returns
false
. If you can support
changing some connection parameters without destroying the connection (for
example, language), override and return
true
.
6.
If you override
isConnectionInfoOverwritable
, consider overriding the boolean
matchConnectionRequestInfo (WBIConnectionRequestInfo)
98
WebSphere Adapters: WebSphere Adapter Toolkit User Guide
Содержание WebSphere Adapters
Страница 1: ...WebSphere Adapters WebSphere Adapter Toolkit User Guide Version 6 Release 2 Version 6 Release 2...
Страница 2: ......
Страница 3: ...WebSphere Adapters WebSphere Adapter Toolkit User Guide Version 6 Release 2 Version 6 Release 2...
Страница 6: ...iv WebSphere Adapters WebSphere Adapter Toolkit User Guide...
Страница 211: ...7 Start UTC using the Run universal test client option WebSphere Adapter development overview 205...
Страница 220: ...214 WebSphere Adapters WebSphere Adapter Toolkit User Guide...
Страница 224: ...218 WebSphere Adapters WebSphere Adapter Toolkit User Guide...
Страница 225: ......
Страница 226: ...Printed in USA...