277
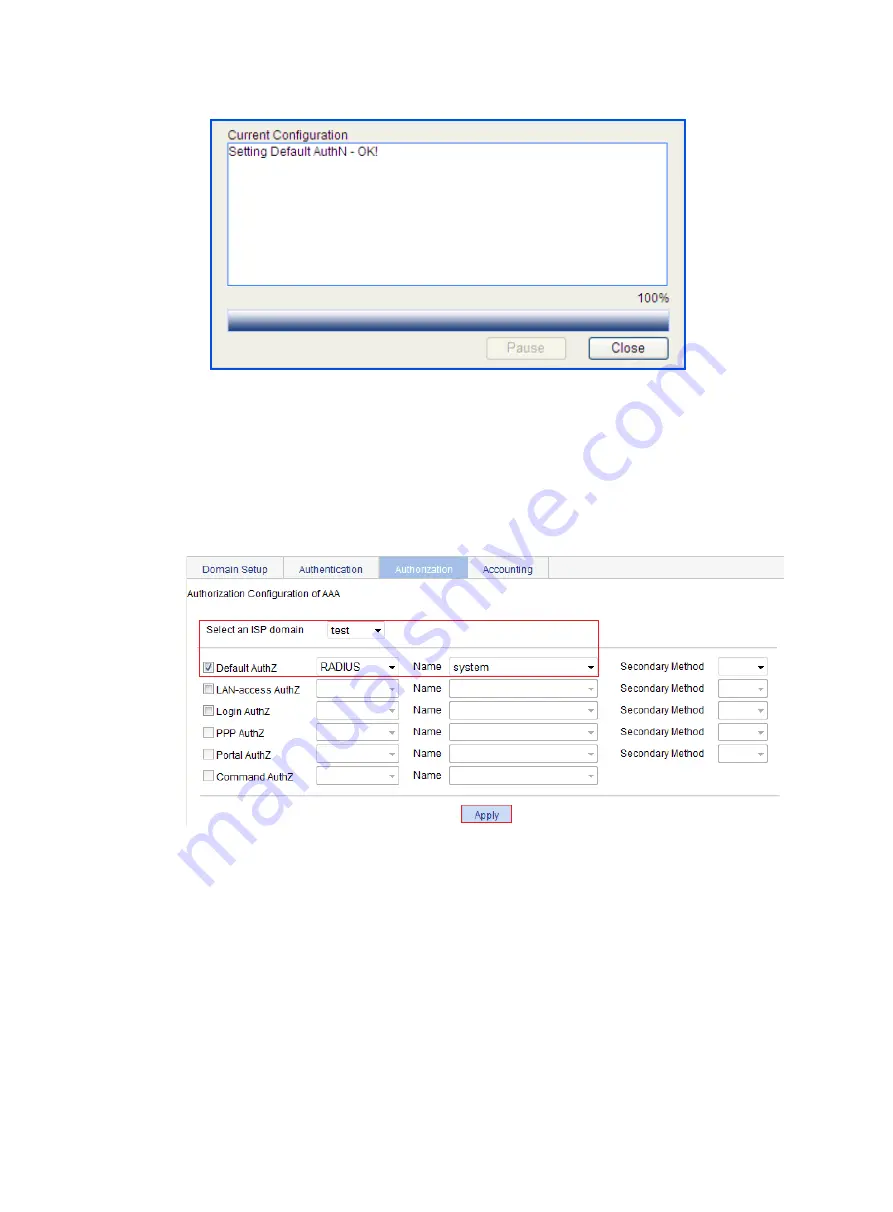
Figure 291 Configuration progress dialog box
e.
After the configuration process is complete, click
Close
.
3.
Configure AAA authorization method for the ISP domain:
a.
Click the
Authorization
tab.
b.
Select
test
from the
Select an ISP domain
list.
c.
Select
Default AuthZ
, select
RADIUS
as the default authorization method, and select the
authorization scheme
system
from the
Name
list, as shown in
.
Figure 292 Configuring the AAA authorization method for the ISP domain
d.
Click
Apply
.
e.
After the configuration process is complete, click
Close
.
4.
Configure AAA accounting method for the ISP domain:
a.
Click the
Accounting
tab.
b.
Select
test
from the
Select an ISP domain
list.
c.
Select
Accounting Optional
and select
Enable
from the list.
d.
Select
Default Accounting
, select the accounting method
RADIUS
, and select the
accounting scheme
system
from the
Name
list.
e.
Click
Apply
.
Содержание FlexNetwork NJ5000
Страница 12: ...x Index 440 ...
Страница 39: ...27 Figure 16 Configuration complete ...
Страница 67: ...55 Figure 47 Displaying the speed settings of ports ...
Страница 78: ...66 Figure 59 Loopback test result ...
Страница 158: ...146 Figure 156 Creating a static MAC address entry ...
Страница 183: ...171 Figure 171 Configuring MSTP globally on Switch D ...
Страница 243: ...231 Figure 237 IPv6 active route table ...
Страница 293: ...281 Figure 298 Ping operation summary ...






























