How To establish an IPSec VPN tunnel with LB-2 VPN
Property of HotBrick — 2005
8
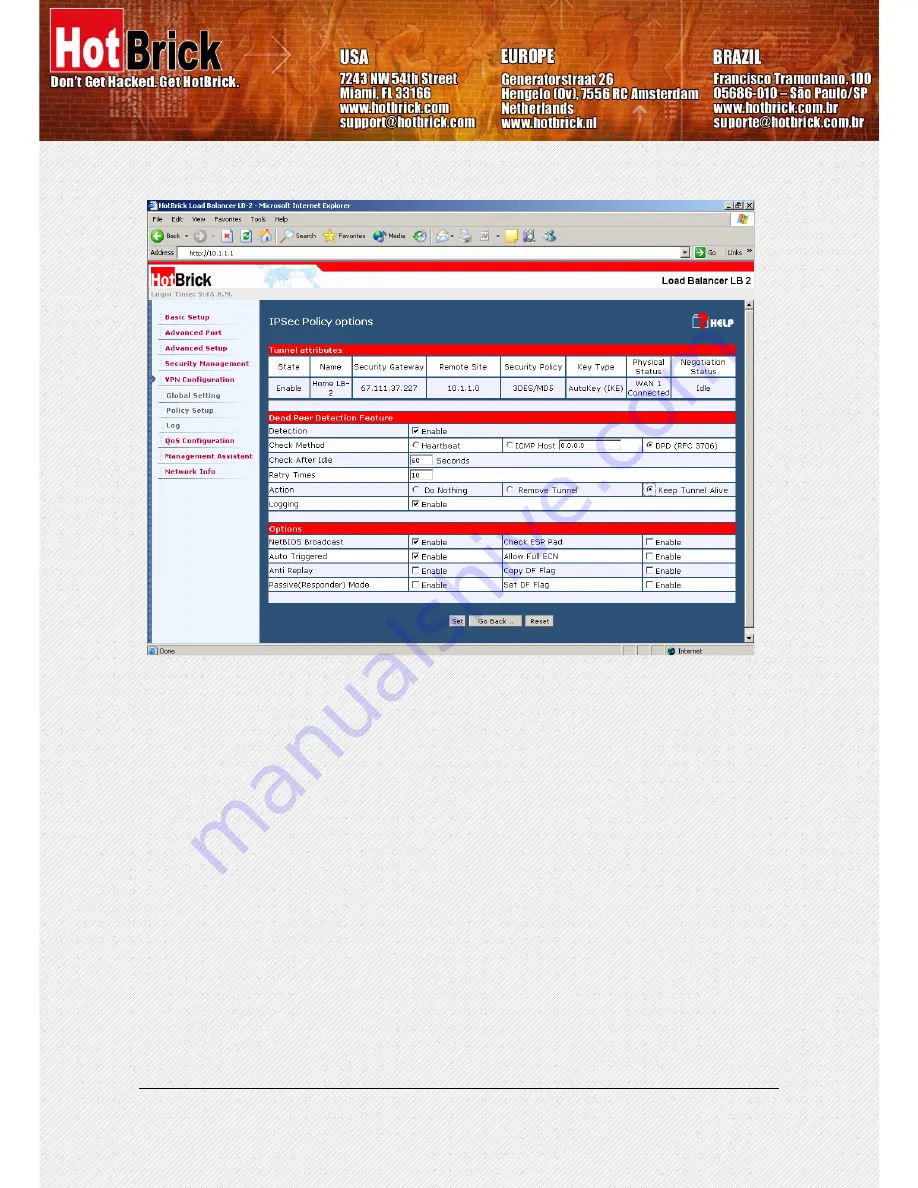
Figure 9 – IPSec Policy Option for Site B
Figures 10 and 11 show the tunnel established under Policy Setup. Figures 11 and 12 show the log
with all the phases of the IPSec tunnel established.