4
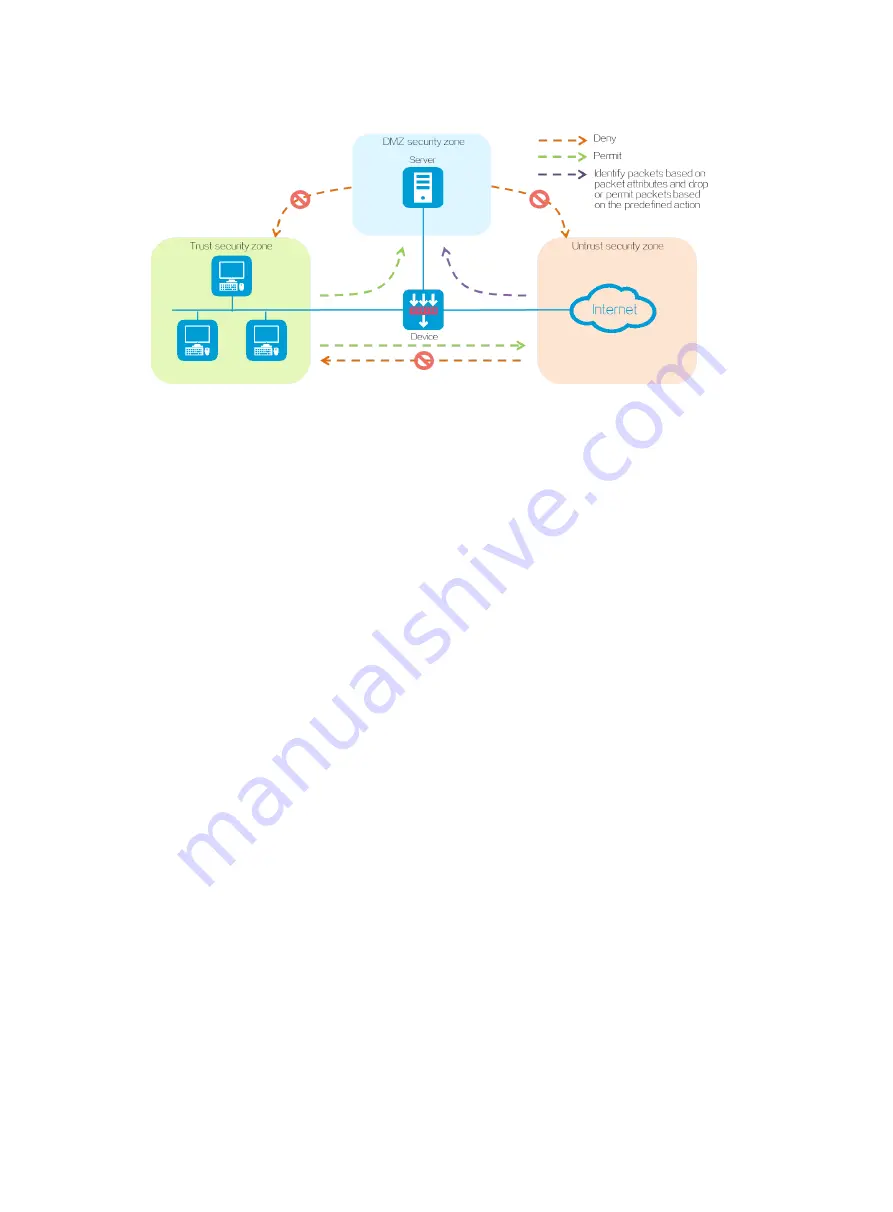
Figure 3 Security zones
A firewall device provides default security zones
Local
,
Management
,
Trust
,
DMZ
, and
Untrust
.
Default security zones cannot be deleted. The function and application scenario of each default
security zone are as follows:
•
Local
—Refers to the device itself. You cannot add interfaces to security zone
Local
. For
communication between a non-Management security zone and the device, you must configure
a security policy to permit the packets between the corresponding security zone and security
zone
Local
.
•
Management
—Refers to the security zone used for managing the device. The device permits
packets between security zones
Management
and
Local
by default and you do not need to
configure a security policy. By default, the device management interface belongs to security
zone
Management.
You can log in to the device management interface to configure the device
from a PC.
•
Trust
—Refers to the trusted security zone. You can assign the interface connected to the
internal network to security zone
Trust
and configure a security policy to perform threat
detection on incoming packets from other security zones. In this way, you can protect internal
hosts and strictly control outgoing packets destined for other security zones to prevent data
leakage.
•
DMZ
—A demilitarized zone is an isolated security zone that typically incorporates the
interfaces connected to various public services or resources (such as Web servers or FTP
servers). You can configure a security policy to audit packets sent to security zone
DMZ
from
other security zones, so as to protect the servers from attacks and prevent data theft.
•
Untrust
—Refers to the untrusted network security zone. You can assign the interface
connected to the Internet to security zone
Untrust
and configure a security policy to strictly
detect packets sent to other security zones, so as to block external attacks and threats such as
viruses.
Содержание SecPath F50X0 Series
Страница 10: ...8 ...
Страница 11: ...9 ...
Страница 12: ...10 ...
Страница 13: ...11 ...
Страница 15: ...13 ...
Страница 16: ...14 ...
Страница 17: ...15 ...
Страница 19: ...17 ...
Страница 20: ...18 ...
Страница 22: ...20 ...
Страница 23: ...21 ...
Страница 24: ...22 ...
Страница 28: ...26 ...
Страница 29: ...27 ...
Страница 30: ...28 Triggering a signature library upgrade ...
Страница 31: ...29 ...
Страница 32: ...30 ...
Страница 33: ...31 ...
Страница 35: ...33 ...
Страница 37: ...35 ...
Страница 38: ...36 Upgrading software Performing maintenance and diagnostics ...





















