Fortress Wireless Access Bridge: Installation
19
omnidirectional or directional antenna. The antenna and
cable must be waterproof.
4
Connect the Bridge's
WAN
port to an external 802.3af PSE/
PoE (Power Sourcing Equipment/Power over Ethernet)
source, which—if the
WAN
port will connect to a satellite link
or a DSL or cable modem—provides an in-line connection
to the necessary network device.
NOTE:
Third par-
ty antennas are
subject to local regulato-
ry requirements. For
outdoor installations,
they must be water-
proof.
To plug in the RJ-45 connector with the boot assembly
installed:
orient the connector correctly with the WAN port,
and then twist the outer ring of the connector boot
clockwise until the channels in the ring align with the
locking studs on the Bridge’s WAN port casing. Continue
twisting the boot’s outer ring clockwise until the locking
channels are fully engaged and the boot is flush with the
port casing. A distinct click in the final turn of the boot’s
outer ring indicates that connector and boot are securely
plugged into the Bridge. (Installing the connector boot
assembly is covered in Section 2.4.3.)
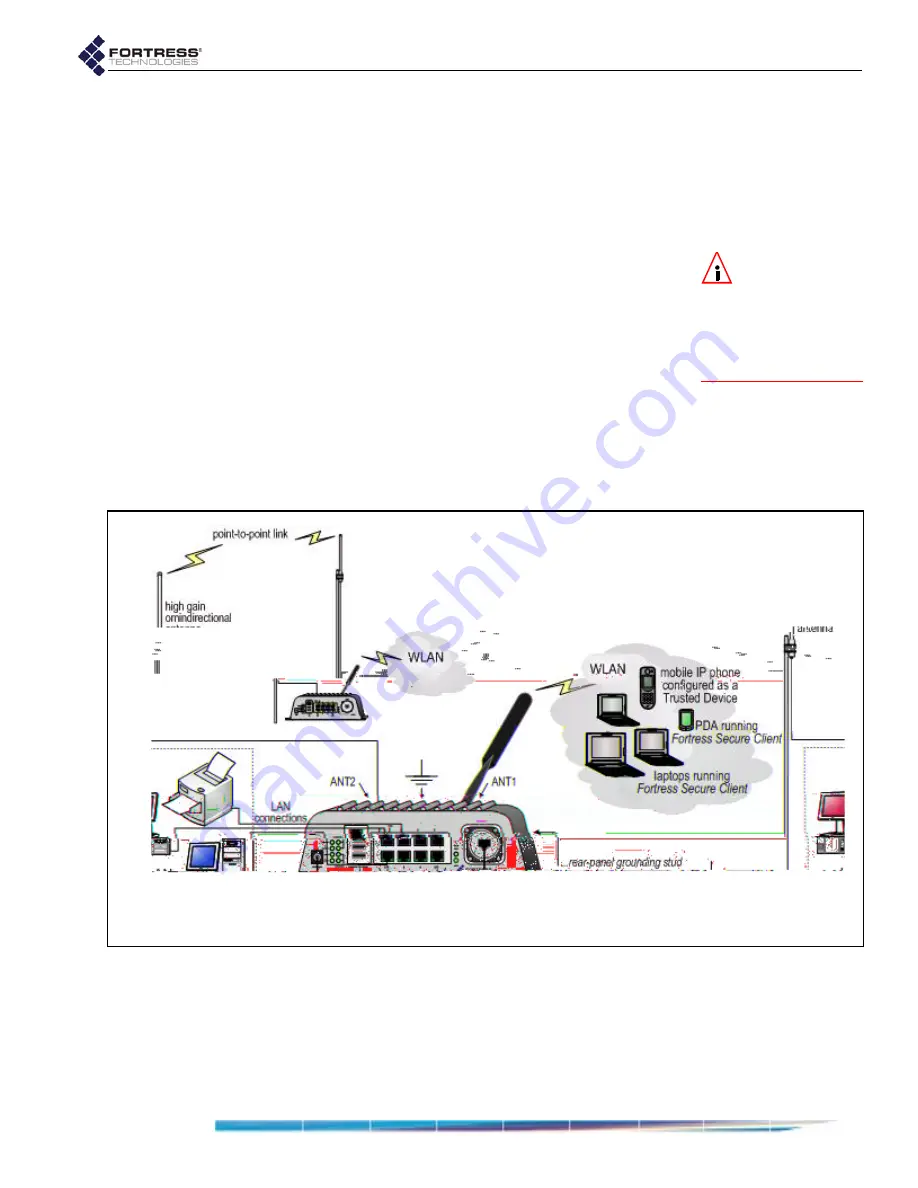
2.5 Indoor Installation
Figure 2.5
Indoor Fortress Bridge Connections
2.5.1
Connecting the Bridge for Indoor Operation
When the Fortress Bridge is installed indoors, it can be located
directly on a desktop with no additional hardware, or it can be
wall mounted, in any orientation—with four, #8, 3/4" wall-
anchored, flathead screws—through the mounting holes in the
chassis’s four corners.
Содержание ecure Wireless Access Bridge
Страница 2: ......
Страница 18: ......
Страница 47: ...Fortress Bridge Configuration 37 NOTE For security ...
Страница 87: ......














































