Policy-based versus route-based VPNs
IPSec VPN
FortiGate Version 4.0 Administration Guide
532
01-400-89802-20090424
For more information about configuring IPSec VPNs, see the
Policy-based versus route-based VPNs
FortiGate units support both policy-based and route-based VPNs. Generally, you can
configure route-based VPNs more easily than policy-based VPNs. However, the two types
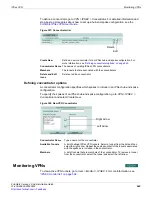
have different requirements that limit where you can use them, as shown in
You create a policy-based VPN by defining an IPSEC firewall policy between two network
interfaces and associating it with the VPN tunnel (phase 1 or manual key) configuration.
You need only one firewall policy, even if either end of the VPN can initiate a connection.
You create a route-based VPN by enabling IPSec interface mode when you create the
VPN phase 1 or manual key configuration. This creates a virtual IPSec interface that is
bound to the local interface you selected. You then define an ACCEPT firewall policy to
permit traffic to flow between the virtual IPSec interface and another network interface. If
either end of the VPN can initiate the connection, you need two firewall policies, one for
each direction.
Virtual IPSec interface bindings are shown on the network interfaces page. (Go to
System
> Network > Interface
.) The names of all tunnels bound to physical, aggregate, VLAN,
inter-VDOM link or wireless interfaces are displayed under their associated interface
names in the Name column. For more information, see
. As with
other interfaces, you can include a virtual IPSec interface in a zone.
Hub-and-spoke configurations
To function as the hub of a hub-and-spoke VPN, the FortiGate unit provides a
concentrator function. This is available only for policy-based VPNs, but you can create the
equivalent function for a route-based VPN in any of the following ways:
•
Define a firewall policy between each pair of IPSec interfaces that you want to
concentrate. This can be time-consuming to maintain if you have many site-to-site
connections, since the number of policies required increases rapidly as the number of
spokes increases.
•
Put all the IPSec interfaces into a zone and then define a single zone-to-zone policy.
•
Put all the IPSec interfaces in a zone and enable intra-zone traffic. There must be more
than one IPSec interface in the zone.
For more information and an example, see the
FortiGate IPSec VPN User Guide
.
Table 54: Comparison of policy-based and route-based VPNs
Policy-based
Route-based
Available in NAT/Route or Transparent
mode
Available only in NAT/Route mode
Requires a firewall policy with IPSEC
action that specifies the VPN tunnel. One
policy controls connections in both
directions.
Requires only a simple firewall policy with
ACCEPT action. A separate policy is required
for connections in each direction.
Содержание Gate 60D
Страница 678: ...Reports Log Report FortiGate Version 4 0 Administration Guide 678 01 400 89802 20090424 http docs fortinet com Feedback...
Страница 704: ...Index FortiGate Version 4 0 Administration Guide 704 01 400 89802 20090424 http docs fortinet com Feedback...
Страница 705: ...www fortinet com...
Страница 706: ...www fortinet com...