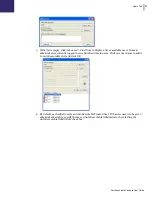
White List Tab
|
29
Anti-Executable Standard User Guide
8. Click
Save
to save the White List. Click
Save As
to save under a different name. White Lists are
saved in a proprietary format with the extension
.aewl
. Click
Export
to export a White List to
XML or CSV format. White Lists in XML or CSV format can be opened and edited through
Windows Explorer but can not be set as the Active White List.
Activating a White List
After a White List has been created, it can be set as the Active White List by clicking the
Browse
button in the
Active White List
section of the
White List
tab. The browse button launches an
Open
dialog. Browse to the White List and click
Open
.
Adding Executables or Folders to an Existing White List using the White List
Editor
In addition to populating a new White List, the Scan feature allows executables from a specific
location to be added to an existing White List. This location can be local, external, or on a network.
•
Click
Scan
to launch the
White List Scan Destination
dialog. This will search the selected
location for any executables. Once the scan has finished, the results can be merged into the
White List.
•
Individual folders and executables can be added by clicking
Add
.
•
To open a previously created White List, click
Open
and browse to the White List file. Make
any changes necessary with
Add
,
Remove, Scan,
or
Merge
buttons. These buttons add and
remove executables and folders from the White List. They do not modify actual files or folders
on the machine.
•
Click the
White List Only
button to delete the executables from the Black List and ensure that
they are a part of only the White List.
•
Multiple White Lists can be opened and edited at the same time. Only one White List can be set
as an Active White List at a time.
For more information about an executable, right-click the executable and select
Google Search
. The default browser is launched and the name of the executable is
searched on www.google.com.
Содержание ANTI-EXECUTABLE STANDARD
Страница 1: ...Anti Executable Standard User Guide 1...
Страница 14: ...Anti Executable Standard User Guide 14 Introduction...
Страница 39: ...Users Tab 39 Anti Executable Standard User Guide...
Страница 42: ...Anti Executable Standard User Guide 42 Using Anti Executable...
Страница 46: ...Anti Executable Standard User Guide 46 Uninstalling Anti Executable...