320
F.1
Introduction
If you want to provide a reliable and easy HTTP scanning service in your
network with F-Secure Internet Gatekeeper, you should use a transparent
proxy. For information about different methods that you can use when
setting up a transparent proxy, see
If you want to ensure that the speed of the communication does not slow
down and is not interrupted when scanning the traffic for malicious code,
you should set up load balancing. For information about different methods
you can use when setting up the HTTP load balancing, see “
.
For more information about load balancing with Windows Network Load
Balancing Service, see “
Load Balancing With Windows Network Load
The section instructs how to set up cluster that
clients can access. Servers in a cluster communicate among themselves
and provide high-availability, load balancing and scalability. The service is
included in any version of Windows 2003 server.
If you want to deploy F-Secure Internet Gatekeeper in an environment
with multiple sub-domains, see“
Deployment Scenarios for Environments
F.2
Transparent Proxy
A proxy server is a system which acts as an agent between the server
and the client. A typical proxy server serves one or multiple Internet
protocols, such as HTTP (Hyper-Text Transfer Protocol) and SMTP
(Simple Mail Transfer Protocol). The proxy server may modify the
requests that pass through it, which provides more functionality for clients.
This proxy technology is used in F-Secure Internet Gatekeeper to
intercept and scan data for viruses and malicious code.
Usually HTTP proxy server is used by specifying the proxy host name and
the port number manually in the web browser and other web-based
software. If the proxy is configured like this, it is not transparent. You may
Содержание INTERNET GATEKEEPER WINDOWS 2000-2003 SERVER 6.61...
Страница 1: ...F Secure Internet Gatekeeper Windows 2000 2003 Server Administrator s Guide...
Страница 10: ...10 ABOUT THIS GUIDE How This Guide is Organized 11 Conventions Used in F Secure Guides 13...
Страница 26: ...26 2 DEPLOYMENT Overview 27 Deployment Scenarios 29...
Страница 58: ...58 Step 10 Enter the IP address of the F Secure Policy Manager Server Click Next to continue...
Страница 200: ...200 Figure 6 17 Summary of SMTP scanning statistics in F Secure Internet Gatekeeper Web Console...
Страница 251: ...251 9 ADMINISTERING F SECURE MANAGEMENT AGENT F Secure Management Agent Settings 252 Configuring Alert Forwarding 254...
Страница 261: ...CHAPTER10 261 Quarantine Management Figure 10 1 Quarantine Query page...
Страница 275: ...275 11 SECURITY AND PERFORMANCE Introduction 276 Optimizing Security 276 Optimizing Performance 277...
Страница 280: ...280 12 UPDATING VIRUS AND SPAM DEFINITION DATABASES Overview 281 Automatic Updates 281 Configuring Automatic Updates 282...
Страница 296: ...296 A APPENDIX Warning Messages HTTP Warning Messages 297 SMTP Warning Messages 298...
Страница 300: ...300 B APPENDIX Specifying Hosts Introduction 301 Domain 301 Subnet 301 IP Address 302 Hostname 302...
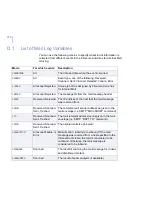
Страница 304: ...304 C APPENDIX Access Log Variables List of Access Log Variables 305...
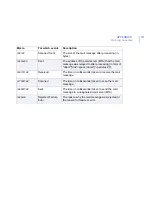
Страница 309: ...309 D APPENDIX Mail Log Variables List of Mail Log Variables 310...
Страница 312: ...312 E APPENDIX Configuring Mail Servers Configuring the Network 313 Configuring Mail Servers 314...
Страница 318: ...318 6 Change the TCP port to some other unused port for example 26 7 Click OK for all the windows and reboot the server...
Страница 360: ...360 G APPENDIX Services and Processes List of Services and Processes 361...
Страница 414: ...414...