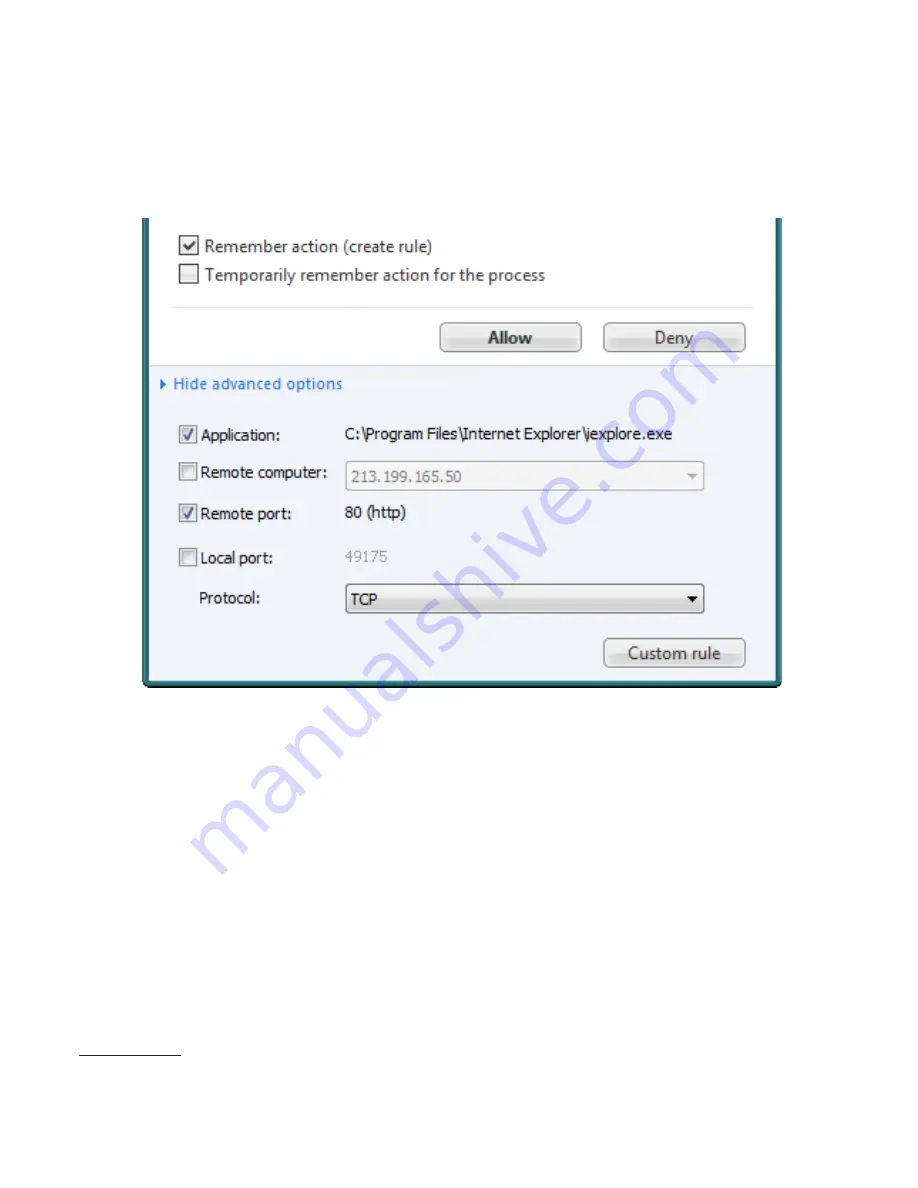
5
Select the
Remember action
option and select
Allow
or
Deny
to create a permanent rule for the
communication. If a similar communication occurs in the future, it is automatically allowed or blocked. However,
such rules are very general, since they would always allow all incoming and outgoing communications (for all
target ports, all IP addresses...) for the given process. To specify more detailed parameters for a specified rule,
click
Show advanced options
. The figure below shows an example of limiting the HTTP communication (port 80)
established by the Internet Explorer web browser.
In addition to port 80 (HTTP), you may wish to allow communication on port 443 (HTTPS). There are three ways
to accomplish this:
o
Wait until the web browser establishes communication on port 443 (e.g., when you log in to your online
banking account). You will be prompted to create an
additional
rule for the same application (Internet Explorer
and the process iexplore.exe).
o
Click
Custom rule
to open a dialog window and specify detailed settings for the rule. You can add specific
ports, IP addresses, IP address ranges, etc. In this case, all communication for the given application would be
specified by only
one
rule.
1
1 If you want an application to behave differently within and outside the Trusted zone, or if you have different rules
exclusively for incoming or outgoing communication (for the same application) more than one rule would be
required.

















