21
•
128-bit WEP Encryption:128-bit WEP keys are as same as the encryption method of 104-bit WEP. You can input 26
hexadecimal digits (0~9, a~f or A~F) or 10 ACSII chars.
The Default Tx Key field determines which of the four keys you want to use in your WLAN environment.
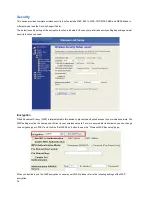
WEP Encryption with 802.1x Setting
The device supports an external RADIUS Server that can secure networks against unauthorized access. If you use the WEP
encryption, you can also use the RADIUS server to check the admission of the users. In this way every user must use a valid
account before accessing the Wireless LAN and requires a RADIUS or other authentication server on the network. An
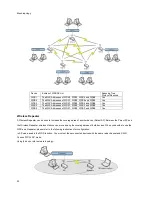
example is shown as follows:
You should choose WEP 64 or 128 bit encryption based on your current network requirements. Then add user accounts and
the target device to the RADIUS server. In the device, you need to specify the IP address, Password (Shared Secret) and Port
number of the target RADIUS server.
Содержание DLB70 Series
Страница 1: ...DLB70XX WLAN Dual Outdoor Radio User Manual Version 1 0 0 11 08 2006...
Страница 28: ...27...
Страница 40: ...39...
Страница 47: ...46 Clone MAC address for Static IP WAN access type Clone MAC address for PPPoE WAN access type...
Страница 48: ...47 Clone MAC address for PPTP WAN access type Physical LAN interface MAC address clone...
Страница 51: ...50 In the Dynamic Routing Table there are two routings for Network 3 and Network 4...
Страница 55: ...54 Configuring VPN...
Страница 66: ...65...