PPTP pass through is only supported in NAT mode.
PPTP client to network pass through
In the configuration shown in
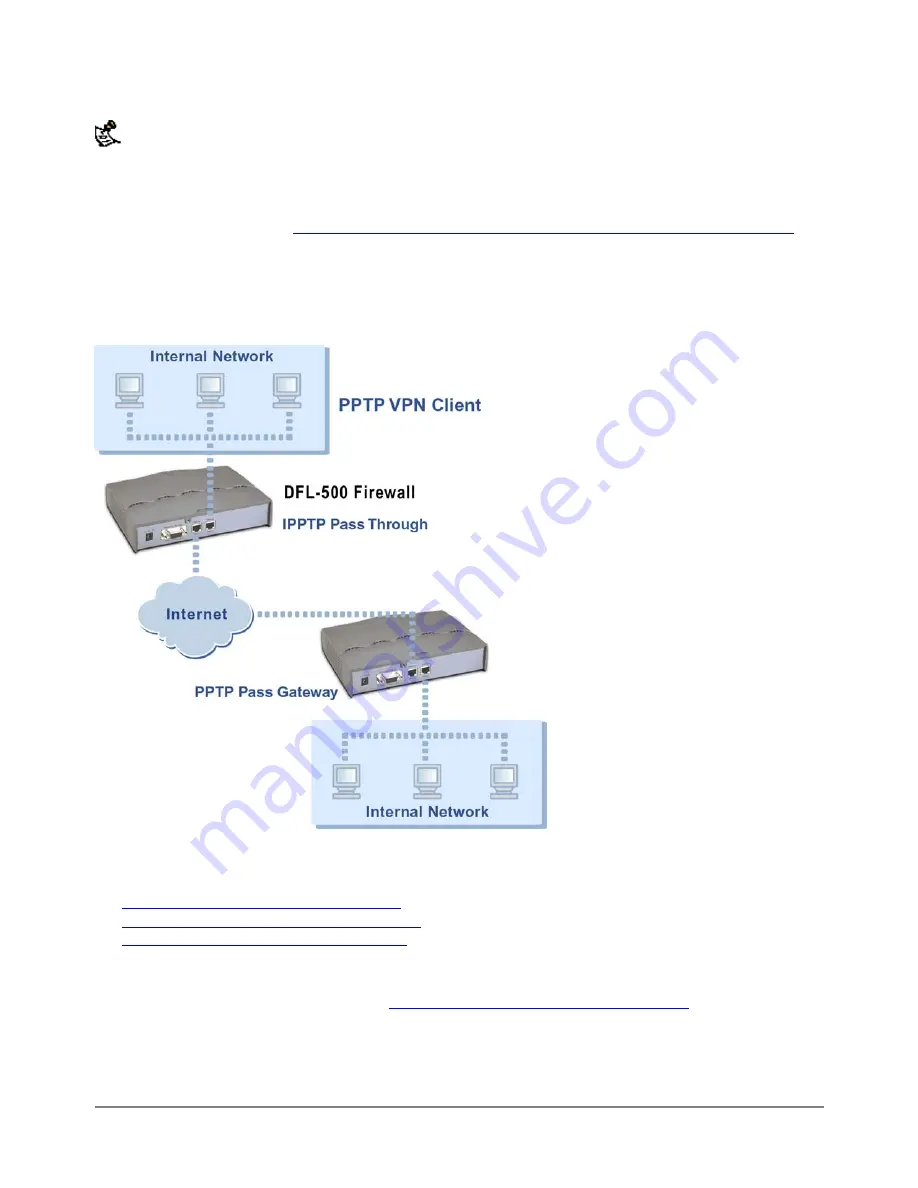
PPTP client connecting to a VPN on the Internet using PPTP pass through
DFL-500 is configured for PPTP pass through. The PPTP VPN client on your internal network runs PPTP
VPN client software to connect to the DFL-500-100 PPTP VPN gateway on the Internet.
You can substitute any suitable DFL-500 product for the PPTP VPN gateway. This gateway could also be a
third-party PPTP VPN gateway.
PPTP client connecting to a VPN on the Internet using PPTP pass through
·
Configure the PPTP VPN client to connect to the destination PPTP VPN gateway as if the client computer
is connected directly to the Internet.
See the following client configuration sections:
Configuring a Windows 98 client for PPTP
Configuring a Windows 2000 Client for PPTP
Configuring a Windows XP Client for PPTP
·
Set the default gateway of the PPTP VPN client computer to the internal interface of the DFL-500 to be
passed through.
·
Configure the PPTP VPN gateway. See
Configuring the DFL-500 as a PPTP gateway
.
·
On the DFL-500 to be passed through, go to
Firewall > Policy
.
·
Select PPTP Pass Through and select Apply.
DFL-500 User Manual
80
Содержание DFL-500
Страница 1: ...DFL 500 V2 27 User Manual D Link Systems Inc DFL 500 User Manual 1 ...
Страница 102: ...DFL 500 User Manual 102 ...
Страница 136: ...DFL 500 User Manual 136 ...
Страница 140: ...Registration Register the D Link DFL 500 Office Firewall online at http www dlink com sales reg DFL 500 User Manual 140 ...




































