Web Cache
99
Web Cache Setup
Select Web cache under Networking. A page similar to the following will be displayed.
Figure 8-1
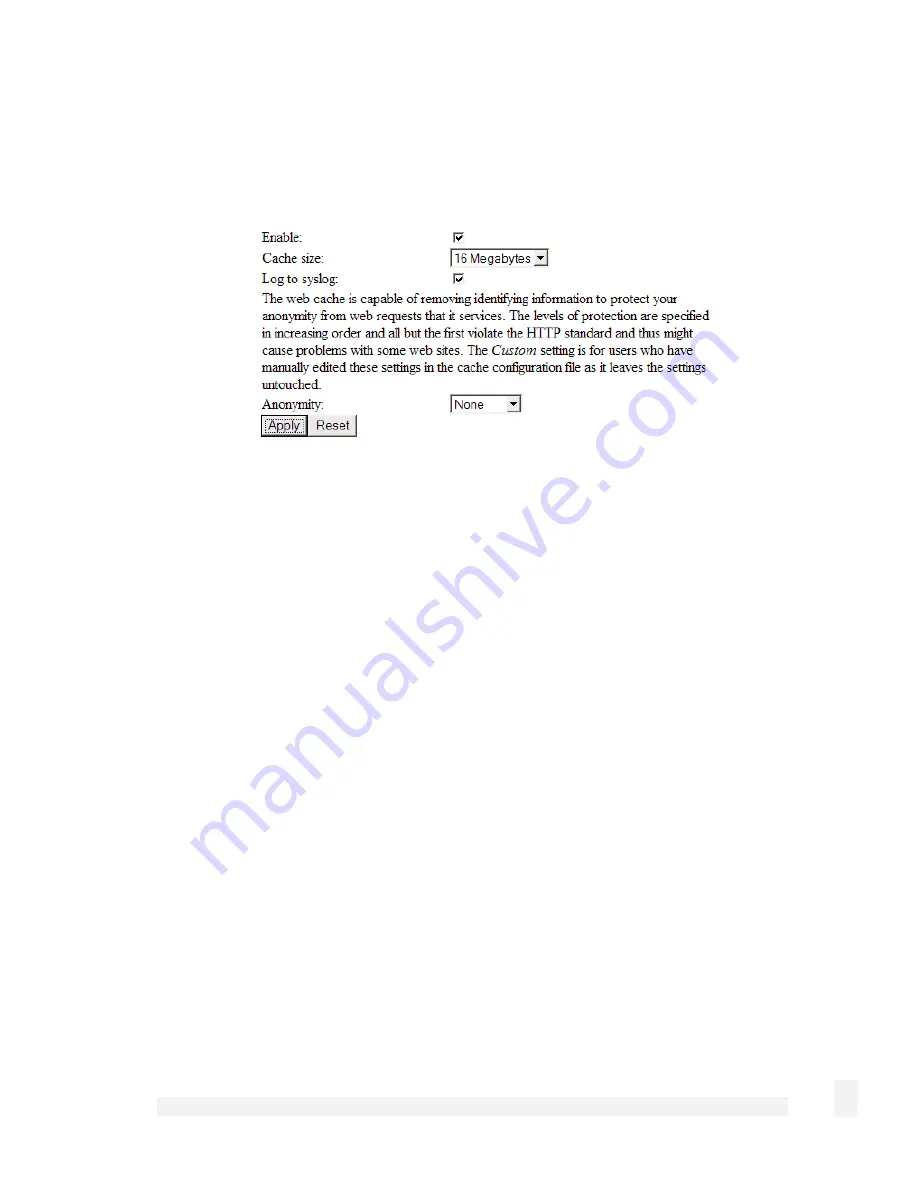
Check Enable to enable the web cache.
Cache size
Select the amount of memory (RAM) on the CyberGuard SG appliance to be reserved for
caching Internet objects. The maximum amount of memory you can safely reserve will
depend on what other services the CyberGuard SG appliance has running, such as VPN
or a DHCP server.
If you will be using a Network Share (recommended, see below), it is generally best to
set this to 8 Megabytes.
If you are unable to use a Network Share, start with a small cache (8 Megabytes or 16
Megabytes) and gradually increase it until you find a safe upper limit where the
CyberGuard SG appliance can still operate reliably.






























