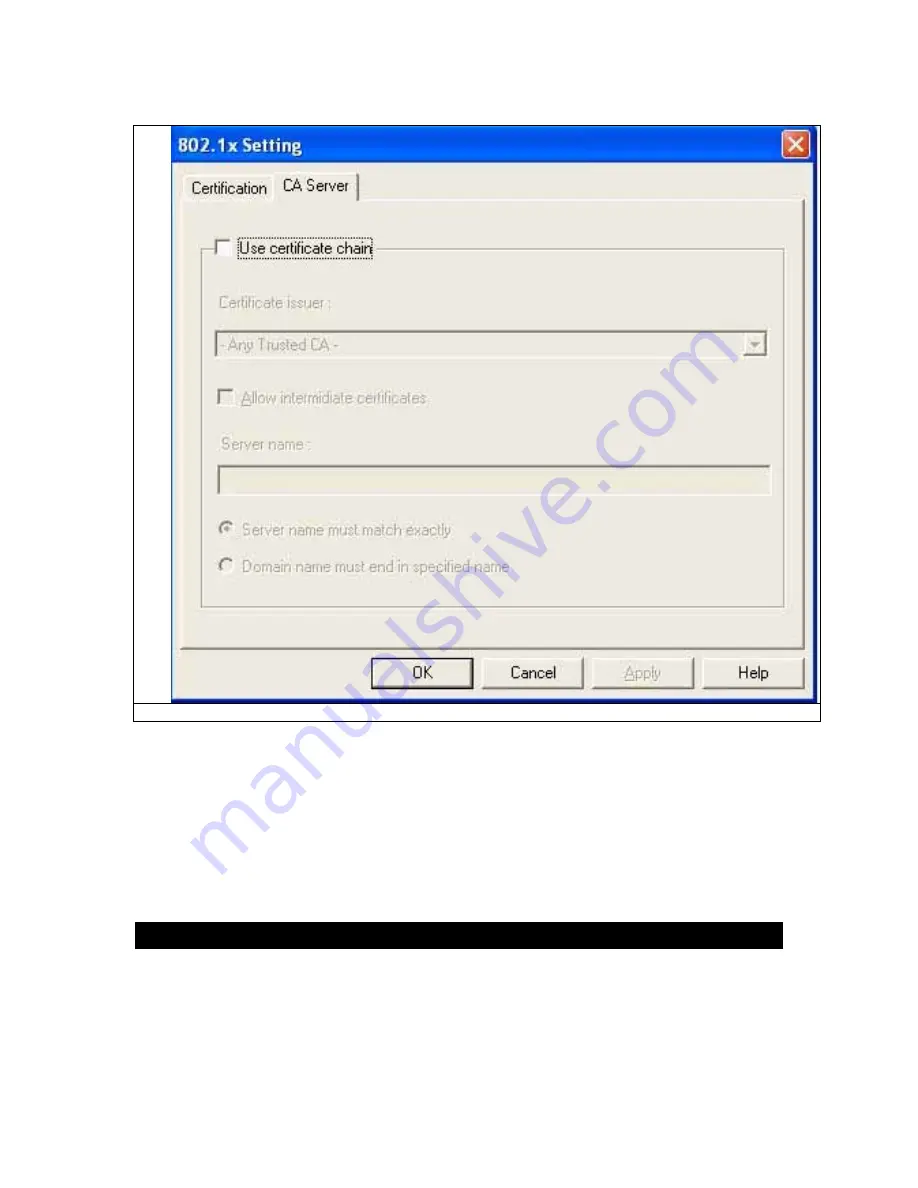
Fig 5-11
1
. Certificate issuer: Choose to use server that is the issuer of certificates.
2
. Allow intermidiate certificates: It must be in the server certificate chain between the server
certificate and the server specified in the certificate issuer must be field.
3
. Server name: Enter the authentication server’s Name..
4.
Please click “OK” to save the profile.
5.5 Link Status
The Link Status (Fig 5-12) provides the link information of the Wireless-G USB Dongle.
The
Status
displays current connection status. If no connection, it will show
Disconnected. Otherwise, the SSID and BSSID will show here.
The
Extra Info
displays link status and current channel in use.






































