13
Step 2: Configure Address Translations on Private Networks
Network Address Translation (NAT) replaces the source IP addresses of network traffic exchanged
between two security appliance interfaces. This translation prevents the private address spaces from
being exposed on public networks and permits routing through the public networks. Port Address
Translation (PAT) is an extension of the NAT function that allows several hosts on the private
networks to map into a single IP address on the public network. PAT is essential for small and medium
businesses that have a limited number of public IP addresses available to them.
To configure NAT between the inside interface and the DMZ interface for the inside HTTP client,
complete the following steps starting from the main ASDM page:
1.
Click the Configuration button at the top of the ASDM window.
2.
Choose the NAT feature on the left side of the ASDM window.
3.
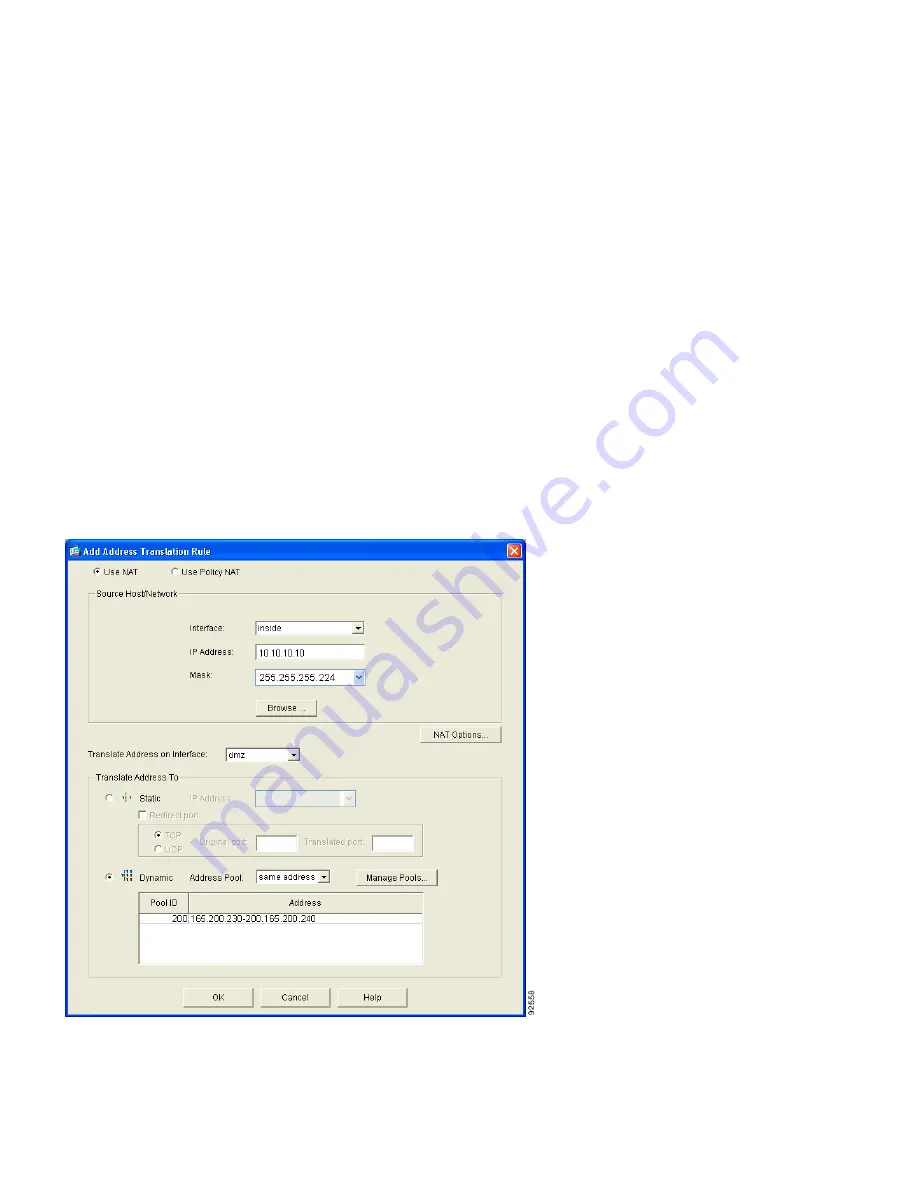
Click the Translation Rules radio button, and then click the Add button at the right side of the
ASDM page. The Add Address Translation Rule window appears.
4.
In the Add Address Translation Rule window, make sure that the Use NAT radio button is
selected, and then choose the inside interface from the drop-down menu.




























