18-17
Cisco ASA Series Firewall CLI Configuration Guide
Chapter 18 ASA IPS Module
Managing the ASA IPS module
Managing the ASA IPS module
This section includes procedures that help you recover or troubleshoot the module.
•
Installing and Booting an Image on the Module, page 18-17
•
Shutting Down the Module, page 18-19
•
Uninstalling a Software Module Image, page 18-20
•
Resetting the Password, page 18-20
•
Reloading or Resetting the Module, page 18-21
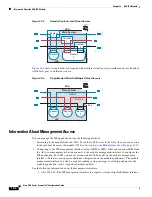
Installing and Booting an Image on the Module
If the module suffers a failure, and the module application image cannot run, you can reinstall a new
image on the module from a TFTP server (for a hardware module), or from the local disk (software
module).
Note
Do not use the
upgrade
command within the module software to install the image.
Step 6
(Optional)
class
name2
Example:
hostname(config-pmap)# class ips_class2
If you created multiple class maps for IPS traffic, you can specify
another class for the policy.
See
Feature Matching Within a Service Policy, page 1-5
for
detailed information about how the order of classes matters within
a policy map. Traffic cannot match more than one class map for
the same action type; so if you want network A to go to sensorA,
but want all other traffic to go to sensorB, then you need to enter
the
class
command for network A before you enter the
class
command for all traffic; otherwise all traffic (including network
A) will match the first
class
command, and will be sent to
sensorB.
Step 7
(Optional)
ips
{
inline
|
promiscuous
} {
fail-close
|
fail-open
} [
sensor
{
sensor_name
|
mapped_name
}]
Example:
hostname(config-pmap-c)# ips promiscuous
fail-close
Specifies that the second class of traffic should be sent to the ASA
IPS module.
Add as many classes as desired by repeating these steps.
Step 8
service-policy
policymap_name
{
global
|
interface
interface_name
}
Example:
hostname(config)# service-policy
tcp_bypass_policy outside
Activates the policy map on one or more interfaces.
global
applies
the policy map to all interfaces, and
interface
applies the policy
to one interface. Only one global policy is allowed. You can
override the global policy on an interface by applying a service
policy to that interface. You can only apply one policy map to
each interface.
Command
Purpose
Содержание ASA 5512-X
Страница 5: ...P A R T 1 Service Policies and Access Control ...
Страница 6: ......
Страница 50: ...3 14 Cisco ASA Series Firewall CLI Configuration Guide Chapter 3 Access Rules History for Access Rules ...
Страница 51: ...P A R T 2 Network Address Translation ...
Страница 52: ......
Страница 126: ...5 28 Cisco ASA Series Firewall CLI Configuration Guide Chapter 5 NAT Examples and Reference DNS and NAT ...
Страница 127: ...P A R T 3 Application Inspection ...
Страница 128: ......
Страница 255: ...P A R T 4 Connection Settings and Quality of Service ...
Страница 256: ......
Страница 288: ...12 14 Cisco ASA Series Firewall CLI Configuration Guide Chapter 12 Quality of Service History for QoS ...
Страница 303: ...P A R T 5 Advanced Network Protection ...
Страница 304: ......
Страница 339: ...P A R T 6 ASA Modules ...
Страница 340: ......
Страница 398: ...17 28 Cisco ASA Series Firewall CLI Configuration Guide Chapter 17 ASA CX Module History for the ASA CX Module ...