5-13
Cisco ASA Series Firewall CLI Configuration Guide
Chapter 5 NAT Examples and Reference
Routing NAT Packets
The Same Address as the Real Address (Identity NAT)
The default behavior for identity NAT has proxy ARP enabled, matching other static NAT rules. You can
disable proxy ARP if desired. You can also disable proxy ARP for regular static NAT if desired, in which
case you need to be sure to have proper routes on the upstream router.
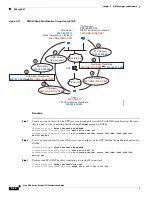
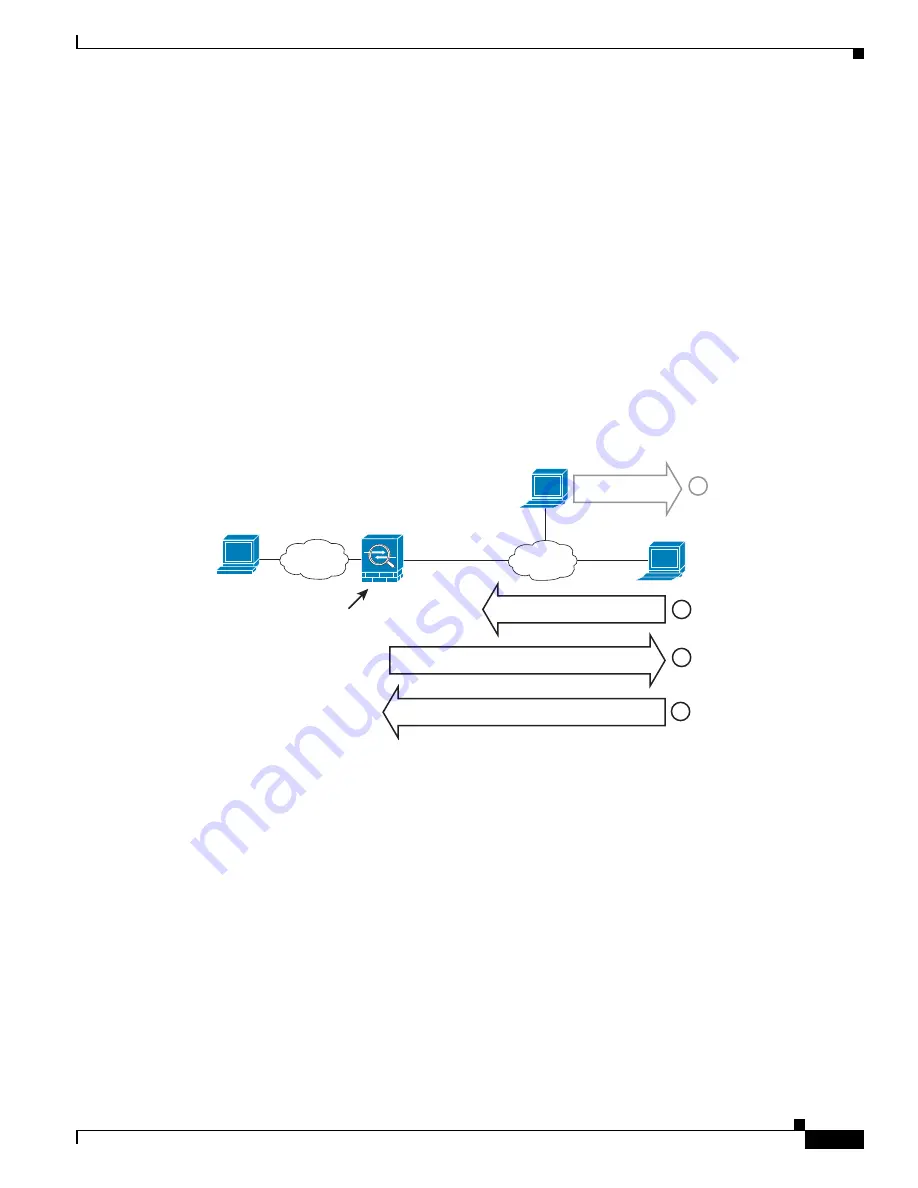
Normally for identity NAT, proxy ARP is not required, and in some cases can cause connectivity issues.
For example, if you configure a broad identity NAT rule for “any” IP address, then leaving proxy ARP
enabled can cause problems for hosts on the network directly connected to the mapped interface. In this
case, when a host on the mapped network wants to communicate with another host on the same network,
then the address in the ARP request matches the NAT rule (which matches “any” address). The ASA will
then proxy ARP for the address, even though the packet is not actually destined for the ASA. (Note that
this problem occurs even if you have a twice NAT rule; although the NAT rule must match both the
source and destination addresses, the proxy ARP decision is made only on the “source” address). If the
ASA ARP response is received before the actual host ARP response, then traffic will be mistakenly sent
to the ASA (see the following figure).
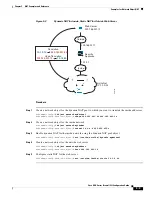
Figure 5-10
Proxy ARP Problems with Identity NAT
In rare cases, you need proxy ARP for identity NAT; for example for virtual Telnet. When using AAA
for network access, a host needs to authenticate with the ASA using a service like Telnet before any other
traffic can pass. You can configure a virtual Telnet server on the ASA to provide the necessary login.
When accessing the virtual Telnet address from the outside, you must configure an identity NAT rule for
the address specifically for the proxy ARP functionality. Due to internal processes for virtual Telnet,
proxy ARP lets the ASA keep traffic destined for the virtual Telnet address rather than send the traffic
out the source interface according to the NAT rule. (See the following figure).
209.165.200.225
209.165.200.2
3
0
209.165.200.2
3
1
Identity NAT for
“
a
ny” with Proxy ARP
O
u
t
s
ide
In
s
ide
1
2
4
ARP for 209.165.200.2
3
0.
Tr
a
ffic incorrectly
s
ent to A
S
A.
Proxy ARP for 209.165.200.2
3
0.
3
ARP Re
s
pon
s
e
Too l
a
te
Содержание ASA 5512-X
Страница 5: ...P A R T 1 Service Policies and Access Control ...
Страница 6: ......
Страница 50: ...3 14 Cisco ASA Series Firewall CLI Configuration Guide Chapter 3 Access Rules History for Access Rules ...
Страница 51: ...P A R T 2 Network Address Translation ...
Страница 52: ......
Страница 126: ...5 28 Cisco ASA Series Firewall CLI Configuration Guide Chapter 5 NAT Examples and Reference DNS and NAT ...
Страница 127: ...P A R T 3 Application Inspection ...
Страница 128: ......
Страница 255: ...P A R T 4 Connection Settings and Quality of Service ...
Страница 256: ......
Страница 288: ...12 14 Cisco ASA Series Firewall CLI Configuration Guide Chapter 12 Quality of Service History for QoS ...
Страница 303: ...P A R T 5 Advanced Network Protection ...
Страница 304: ......
Страница 339: ...P A R T 6 ASA Modules ...
Страница 340: ......
Страница 398: ...17 28 Cisco ASA Series Firewall CLI Configuration Guide Chapter 17 ASA CX Module History for the ASA CX Module ...