10-12
Cisco ASA Series Firewall CLI Configuration Guide
Chapter 10 NAT Examples and Reference
Routing NAT Packets
•
Transparent Mode Routing Requirements for Remote Networks, page 10-14
•
Determining the Egress Interface, page 10-14
Mapped Addresses and Routing
When you translate the real address to a mapped address, the mapped address you choose determines
how to configure routing, if necessary, for the mapped address.
See additional guidelines about mapped IP addresses in
Additional Guidelines for NAT, page 9-8
The following topics explain the mapped address types:
•
Addresses on the Same Network as the Mapped Interface, page 10-12
•
Addresses on a Unique Network, page 10-12
•
The Same Address as the Real Address (Identity NAT), page 10-13
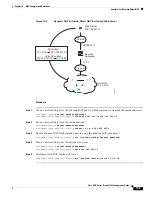
Addresses on the Same Network as the Mapped Interface
If you use addresses on the same network as the mapped interface, the ASA uses proxy ARP to answer
any ARP requests for the mapped addresses, thus intercepting traffic destined for a mapped address. This
solution simplifies routing because the ASA does not have to be the gateway for any additional networks.
This solution is ideal if the outside network contains an adequate number of free addresses, a
consideration if you are using a 1:1 translation like dynamic NAT or static NAT. Dynamic PAT greatly
extends the number of translations you can use with a small number of addresses, so even if the available
addresses on the outside network is small, this method can be used. For PAT, you can even use the IP
address of the mapped interface.
Note
If you configure the mapped interface to be any interface, and you specify a mapped address on the same
network as one of the mapped interfaces, then if an ARP request for that mapped address comes in on a
different
interface, then you need to manually configure an ARP entry for that network on the ingress
interface, specifying its MAC address (see the
arp
command). Typically, if you specify any interface for
the mapped interface, then you use a unique network for the mapped addresses, so this situation would
not occur.
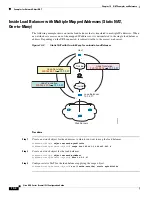
Addresses on a Unique Network
If you need more addresses than are available on the mapped interface network, you can identify
addresses on a different subnet. The upstream router needs a static route for the mapped addresses that
points to the ASA. Alternatively for routed mode, you can configure a static route on the ASA for the
mapped addresses using any IP address on the destination network as the gateway, and then redistribute
the route using your routing protocol. For example, if you use NAT for the inside network (10.1.1.0/24)
and use the mapped IP address 209.165.201.5, then you can configure the following static route that can
be redistributed:
route inside 209.165.201.5 255.255.255.255 10.1.1.99
For transparent mode, if the real host is directly-connected, configure the static route on the upstream
router to point to the ASA: specify the bridge group IP address. For remote hosts in transparent mode,
in the static route on the upstream router, you can alternatively specify the downstream router IP address.
Содержание ASA 5508-X
Страница 11: ...P A R T 1 Access Control ...
Страница 12: ......
Страница 60: ...4 14 Cisco ASA Series Firewall CLI Configuration Guide Chapter 4 Access Rules History for Access Rules ...
Страница 157: ...P A R T 2 Network Address Translation ...
Страница 158: ......
Страница 204: ...9 46 Cisco ASA Series Firewall CLI Configuration Guide Chapter 9 Network Address Translation NAT History for NAT ...
Страница 232: ...10 28 Cisco ASA Series Firewall CLI Configuration Guide Chapter 10 NAT Examples and Reference DNS and NAT ...
Страница 233: ...P A R T 3 Service Policies and Application Inspection ...
Страница 234: ......
Страница 379: ...P A R T 4 Connection Management and Threat Detection ...
Страница 380: ......
Страница 400: ...16 20 Cisco ASA Series Firewall CLI Configuration Guide Chapter 16 Connection Settings History for Connection Settings ...
Страница 414: ...17 14 Cisco ASA Series Firewall CLI Configuration Guide Chapter 17 Quality of Service History for QoS ...