5-11
Cisco Wireless LAN Controller Configuration Guide
OL-17037-01
Chapter 5 Configuring Security Solutions
Configuring RADIUS
d.
If you enabled Active fallback mode in
, enter the probe interval value (in seconds) in the
Interval in Sec field. The interval serves as inactive time in passive mode and probe interval in active
mode. The valid range is 180 to 3600 seconds, and the default value is 300 seconds.
Step 24
To specify the order of authentication when multiple databases are configured, click
Security
>
Priority
Order
>
Management User
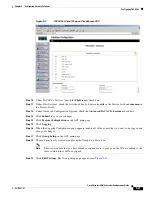
. The Priority Order > Management User page appears (see
).
Figure 5-5
Priority Order > Management User Page
Step 25
For Authentication Priority, choose either
Radius
or
to specify which server has priority over
the other when the controller attempts to authenticate management users. By default, the local database
is always queried first. If the username is not found, the controller switches to the server if
configured for or to the RADIUS server if configured for Radius. The default setting is local
and then Radius.
Step 26
Click
Apply
to commit your changes.
Step 27
Click
Save Configuration
to save your changes.
Using the CLI to Configure RADIUS
Using the controller CLI, follow these steps to configure RADIUS.
Note
“Using the GUI to Configure RADIUS” section on page 5-6
for the valid ranges and default
values of the parameters used in the CLI commands.
Step 1
To specify whether the IP address, system MAC address, or AP MAC address of the originator will be
sent to the RADIUS server in the Access-Request message, enter this command:
config radius callStationIdType
{
ip_address
,
mac_address
,
ap_mac_address
,
ap_macaddr_ssid
}
Step 2
Use these commands to configure a RADIUS authentication server:
•
config radius auth add
index
server_ip_address port#
{
ascii
|
hex
}
shared_secret
—Adds a
RADIUS authentication server.
•
config radius auth keywrap {enable
|
disable
}—Enables AES key wrap, which makes the shared
secret between the controller and the RADIUS server more secure. AES key wrap is designed for
Federal Information Processing Standards (FIPS) customers and requires a key-wrap compliant
RADIUS authentication server.