Aruba Instant 6.5.0.0-4.3.0.0 | User Guide
Intrusion Detection |
327
Chapter 26
Intrusion Detection
The Intrusion Detection System (IDS) is a feature that monitors the network for the presence of unauthorized
IAPs and clients. It also logs information about the unauthorized IAPs and clients, and generates reports based
on the logged information.
The IDS feature in the Instant network enables you to detect rogue IAPs, interfering IAPs, and other devices
that can potentially disrupt network operations.
This chapter describes the following procedures:
l
Detecting and Classifying Rogue IAPs on page 327
l
l
Configuring Wireless Intrusion Protection and Detection Levels on page 328
l
Detecting and Classifying Rogue IAPs
A rogue IAP is an unauthorized IAP plugged into the wired side of the network.
An interfering IAP is an IAP seen in the RF environment but it is not connected to the wired network. While the
interfering IAP can potentially cause RF interference, it is not considered a direct security threat, because it is
not connected to the wired network. However, an interfering IAP may be reclassified as a rogue IAP.
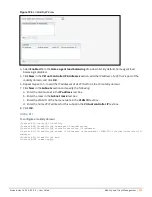
To detect the rogue IAPs, click the
IDS
link in the Instant main window. The built-in IDS scans for access points
that are not controlled by the VC. These are listed and classified as either Interfering or Rogue, depending on
whether they are on a foreign network or your network.
Figure 95
Intrusion Detection
OS Fingerprinting
The OS Fingerprinting feature gathers information about the client that is connected to the Instant network to
find the operating system that the client is running on. The following is a list of advantages of this feature:
l
Identifying rogue clients—Helps to identify clients that are running on forbidden operating systems.
l
Identifying outdated operating systems—Helps to locate outdated and unexpected OS in the company
network.
l
Locating and patching vulnerable operating systems—Assists in locating and patching specific operating
system versions on the network that have known vulnerabilities, thereby securing the company network.
OS Fingerprinting is enabled in the Instant network by default. The following operating systems are identified
by Instant: